EvilProxy, known as the “LockBit of phishing,” is a popular phishing kit used in over a million attacks each month. It allows cybercriminals to launch ransomware infections, steal data, and compromise business emails.
A threat actor recently impersonated Google through a fake ad for the Google Authenticator, a popular multi-factor authentication program. This resulted in innocent users unknowingly downloading malware or falling victim to phishing scams.
Attackers disguise malicious tools as legitimate GenAI apps through phishing sites, web browser extensions, fake apps on mobile stores, and malicious ads on social media.
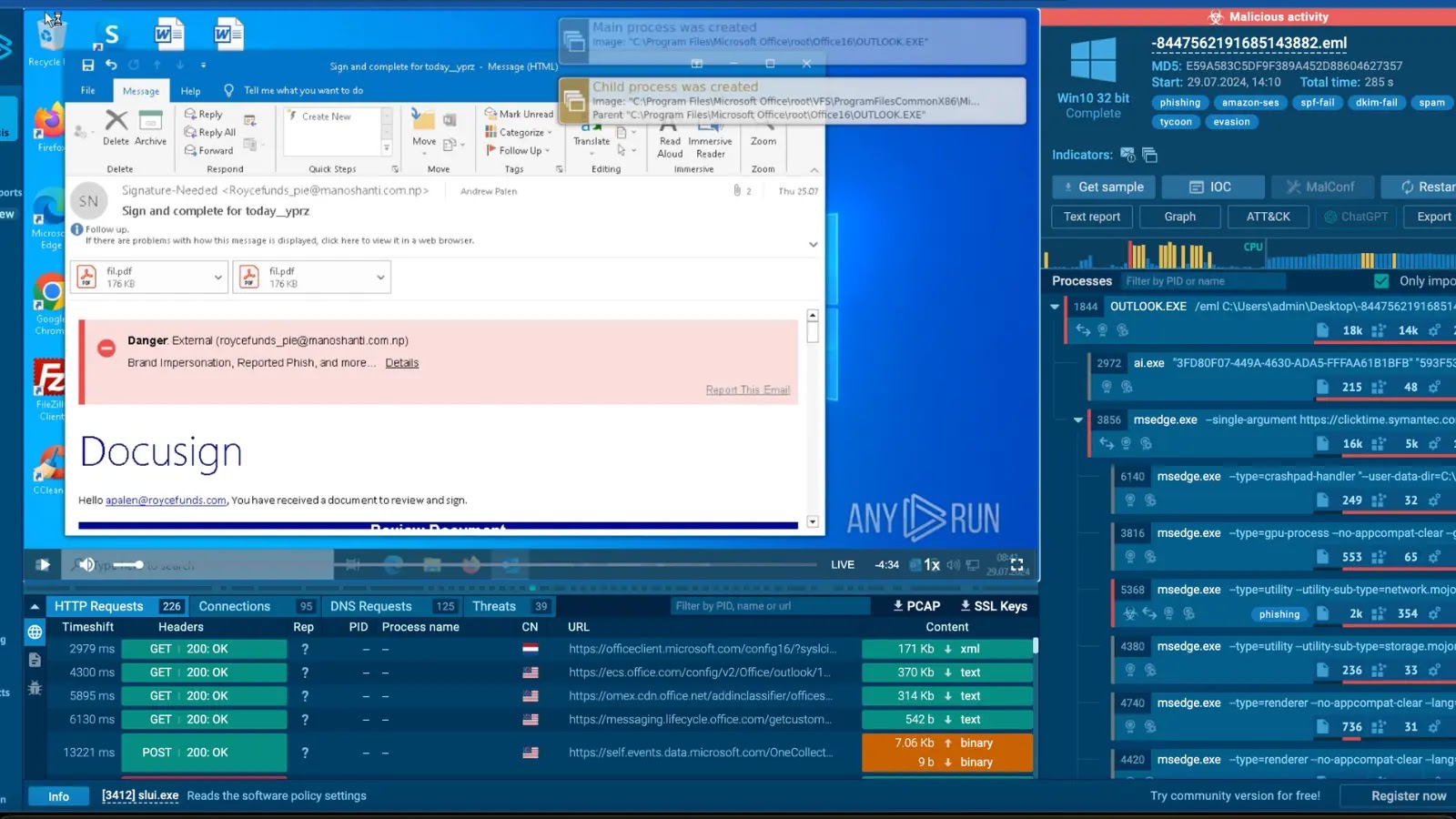
The attack begins with emails from an Amazon SES client containing empty PDF attachments and a message from Docusign. Despite some checks failing, the emails can still appear legitimate due to the compromised source.
The notorious Trik botnet, aka Phorpiex, is being sold in antivirus circles, offering advanced capabilities to evade detection. This C++ botnet includes modules such as a crypto clipper, a USB emitter, and a PE infector targeting crypto wallets.
Multiple SMTP servers are vulnerable to spoofing attacks that allow hackers to bypass authentication. Two vulnerabilities, CVE-2024-7208 and CVE-2024-7209, exploit weaknesses in authentication and verification mechanisms provided by SPF and DKIM.
Ubuntu has fixed two vulnerabilities in OpenVPN, a virtual private network software. These vulnerabilities could keep the closing session active or lead to denial of service. Canonical released security updates for affected Ubuntu releases.
Cybercriminals targeted Polish businesses with Agent Tesla and Formbook malware through widespread phishing campaigns in May 2024. Small and medium-sized businesses (SMBs) in Poland, Italy, and Romania have been affected.
The Blue Report 2024 highlights alarming findings, with 40% of environments vulnerable to total takeover, emphasizing the importance of cybersecurity. Prevention effectiveness has improved to 69%, but detection effectiveness has dropped to 12%.
Breaches impacted 17 industries across 16 countries and regions, with costs related to detecting breaches, notifying victims, post-breach response efforts, and lost business.