A bug hunter discovered a bypass in Meta’s Prompt-Guard-86M model by inserting character-wise spaces between English alphabet characters, rendering the classifier ineffective in detecting harmful content.
The U.S. State Department emphasized the importance of including human rights protections in the upcoming United Nations cybercrime treaty. The final round of negotiations for the treaty, which began on Monday and will conclude on August 9, 2024.
The recent attacks by the SideWinder APT group use phishing lures related to emotional topics like sexual harassment and salary cuts to trick victims into opening booby-trapped Microsoft Word documents.
Change Healthcare has started the process of notifying millions of Americans affected by a massive cyberattack and data theft that occurred more than five months ago. The company is sending individual breach notification letters on a rolling basis.
The newly discovered backdoor has limited samples available on VirusTotal, making detection more difficult. It operates by collecting system information and sending it to a command and control server, awaiting further instructions.
This investment will allow Cowbell to expand its operations, enter key global markets, enhance cyber resilience services, introduce innovative products, and strengthen partnerships.
The European Central Bank has completed a cyber stress test for the banking sector, finding that while banks have strong response frameworks, there is still room for improvement in recovery capabilities.
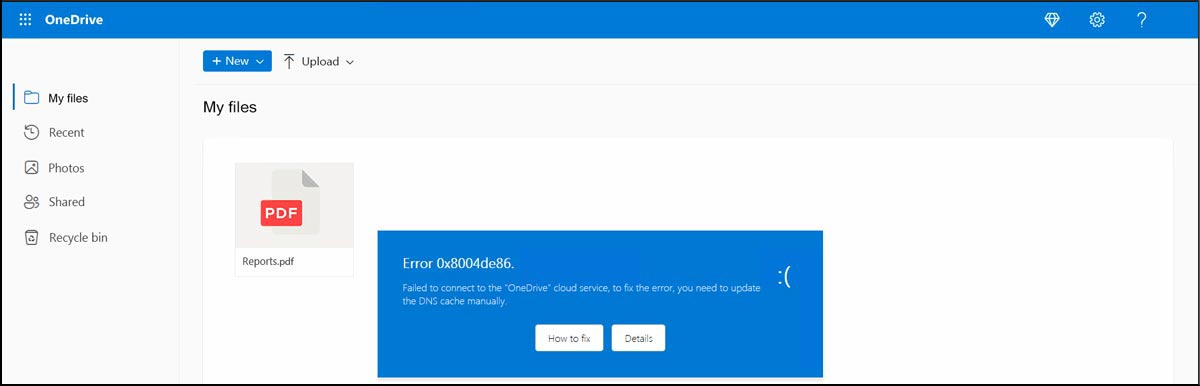
The attackers use social engineering tactics to get users to run a PowerShell script, compromising their systems. The scam starts with an email containing an HTML file that tricks the recipient into clicking on a button to fix a fake DNS issue.
The campaign began in January 2024 and peaked at 14 million emails in June. The emails were designed to steal sensitive information and included authentic-looking signatures to bypass security measures.
The phishing campaigns involve sending fake emails that appear to be from Microsoft, leading recipients to malicious Microsoft Forms impersonating Microsoft 365 or Adobe login pages.