Patchwork hackers targeted Bhutan using the advanced Brute Ratel C4 tool, along with an updated backdoor called PGoShell. This marks the first time Patchwork has been observed using the red teaming software.
Email security gaps in gateway defenses have allowed phishing hackers to sneak malware past static scanning functions. Hackers hid malicious attachments by using a decoy file extension in a compressed archive.
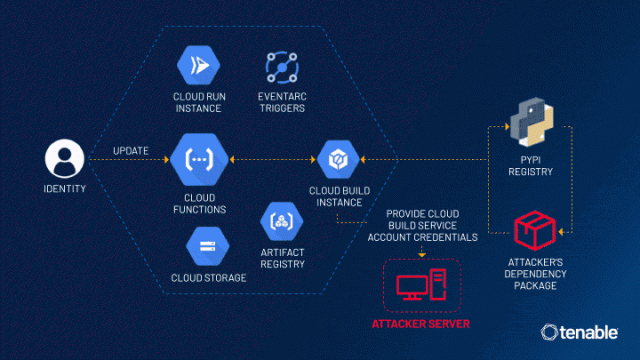
Researchers have uncovered a vulnerability in Google Cloud Platform’s Cloud Functions service called ConfusedFunction. This flaw allows an attacker to escalate their privileges to access other services and sensitive data in an unauthorized manner.
North Korean hackers, specifically the Andariel hacking group, are now targeting the healthcare, energy, and financial sectors according to a Mandiant report. This group is believed to be associated with North Korea’s Reconnaissance General Bureau.
The malicious file, disguised as “Recommendation for the award of President’s.docm,” contained a VBA script that executed the CrimsonRAT remote control program, capable of stealing sensitive information.
According to a Seemplicity survey, AI is speeding up code development faster than security teams can keep up, leading to concerns about vulnerability management. 91% of organizations are increasing their security budgets.
The critical vulnerability in Docker Engine, identified as CVE-2024-41110 with a severity score of 10/10, was first discovered in 2018 and reappeared due to a missed patch in January 2019. It allows attackers to bypass authorization plugins.
The 2024 Mid-Year Cyber Threat Report from SonicWall revealed a 30% increase in malware-based threats compared to 2023, with a significant spike in attacks from March to May, including 78,923 new variants observed in the first half of 2024.
Stargazer Goblin has been distributing various malware families like Atlantida Stealer, Lumma, and Rhadamanthys, since at least August 2022. The threat actor charges users to “star” repositories with fake accounts, increasing their credibility.
Okta Browser Plugin versions 6.5.0 through 6.31.0 are vulnerable to cross-site scripting, prompting users to save credentials in Okta Personal. The issue was fixed in version 6.32.0 for Chrome, Edge, Firefox, and Safari.