The popularity of stolen data bazaar BreachForums surged after it was used to sell a giant database of stolen information describing Chinese citizens, threat intelligence firm Cybersixgill said on Thursday.
The U.S. Justice Department is investigating a cyber breach involving the federal court records management system, the department’s top national security attorney told lawmakers on Thursday.
Kaspersky observed a UEFI rootkit malware, dubbed CosmicStrand, on machines with ASUS and Gigabyte motherboards. CosmicStrand has a lengthy, intricate execution chain to infect Windows machines with a kernel-mode implant while remaining undetected and persist in a system as long as feasible.
Researchers discovered a zero-day vulnerability affecting older versions of PrestaShop websites. The bug can be exploited to harvest customers’ payment information. After the attack, the remote attackers erase their traces that stops the site owner from knowing that they were breached. Experts suggest disabling the MySQL Smarty cache storage features until a patch is issued.
APT37 is targeting high-value organizations in Poland, the Czech Republic, and other European countries, with Konni RAT. The campaign is dubbed STIFF#BIZON. The attacked phishing document is a decoy and seems to be a report from a Russian war correspondent, Olga Bozheva. Researchers have shared some recommendations to mitigate threats.
Software cracks and keygen sites could be attractive but it’s extremely unsafe. A malware campaign by SmokeLoader operators was spotted dropping the Amadey Bot, a rarely used malware since 2020, via similar lures. Users should avoid downloading from unauthenticated sources and double check domains they are accessing for software downloading.
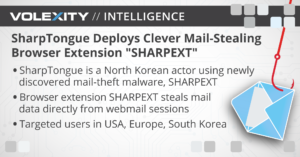
This actor is believed to be North Korean in origin and is often publicly referred to under the name Kimsuky. The definition of which threat activity comprises Kimsuky is a matter of debate amongst threat intelligence analysts.
Every European telecom operator that suffers a security incident, notifies its national authorities which share a summary of these reports to ENISA at the start of every calendar year.
Poor training is hindering companies’ ability to protect themselves from cybersecurity risks, according to a report from Tessian. Three in four companies in the UK and US have experienced a security incident in the last year.
These websites have the capability to change their background and logo depending on the user’s domain. The phishing sites are stored in the InterPlanetary File System (IPFS).