Researchers from Kaspersky have named the backdoor SessionManage, which was first spotted the threat in early 2022. It is a native-code module for Microsoft’s IIS web server software.
In a recent document, the DoJ said that it pledges to increase “the percentage of reported ransomware incidents from which cases are opened, added to existing cases, or resolved or investigative actions are conducted within 72 hours to 65%.”
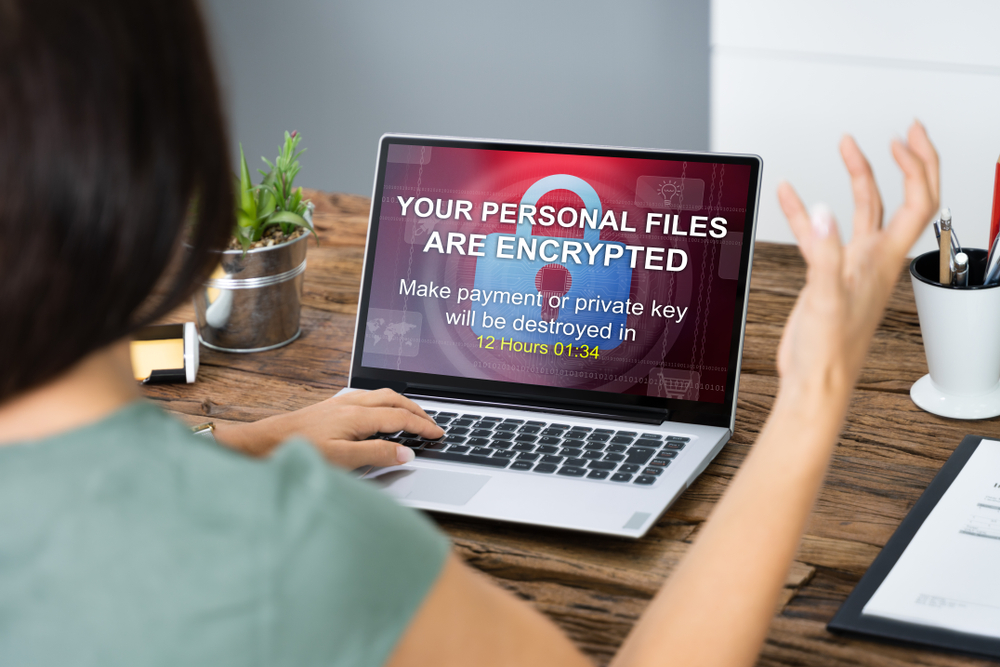
The southern Maastricht University in 2019 was hit by a large cyberattack in which criminals used ransomware, a type of malicious software that locks valuable data and can only be accessed once the victim pays a ransom amount.
As of May 2022, the operators of the ransomware are heavily relying on vulnerabilities in Remote Desktop Protocol (RDP) endpoints to access victims’ networks.
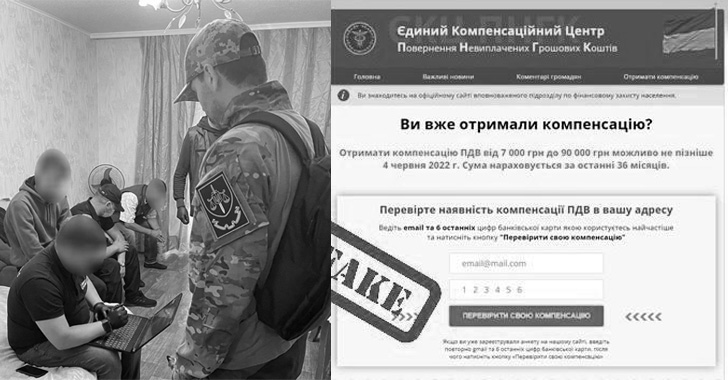
The Cyber Police of Ukraine apprehended nine members of a criminal gang that used hundreds of phishing sites that claimed to offer financial assistance to Ukrainian citizens as part of a campaign aimed at capitalizing on the ongoing conflict.
A hacker has claimed to have procured a trove of personal information from the Shanghai police on one billion Chinese citizens, which tech experts say, if true, would be one of the biggest data breaches in history.
Tracked as CVE-2022-34265, the potential SQL Injection vulnerability impacts Django’s main branch, and versions 4.1 (currently in beta), 4.0, and 3.2, with patches and new releases issued that squash the vulnerability.
Avast security researchers have discovered a server on Discord where a group of minors is involved in developing, upgrading, marketing, and selling malware and ransomware strains on the platform, supposedly to earn pocket money.
Security researchers have published technical details and proof-of-concept exploit code for CVE-2022-28219, a critical vulnerability in the Zoho ManageEngine ADAudit Plus tool for monitoring activities in the Active Directory.
Professor Edward Burke made the comment following the report of High Court judge Charles Meenan, who supervises the interception of phone calls and post, and access to traffic data on private communications.