The malware, dubbed Trojan.Clipminer, leverages the compute power of compromised systems to mine for cryptocurrency as well as identify crypto-wallet addresses in clipboard text and replace it to redirect transactions.
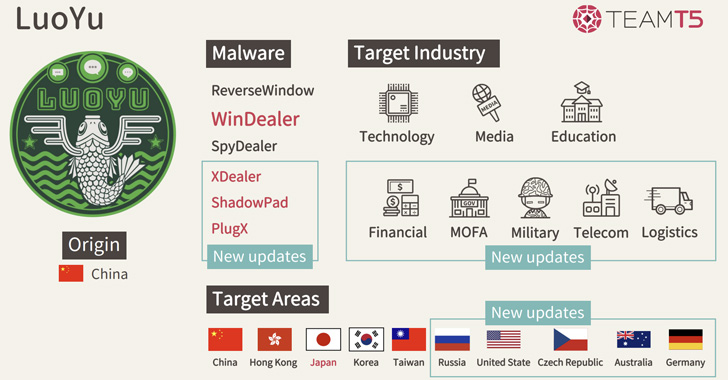
An “extremely sophisticated” Chinese-speaking advanced persistent threat (APT) actor dubbed LuoYu has been observed using a malicious Windows tool called WinDealer that’s delivered by means of man-on-the-side attacks.
On the heels of similar announcements by YL Ventures and SYN Ventures, Ten Eleven this week announced it had raised $600 million for its third generation fund to invest in the next wave of security companies, from seed to growth stages.
The data breach happened due to a misconfigured database owned by ACY Securities. The worse part of the data leak is the fact that it contained over 60GB worth of data that was left exposed without any security authentication.
The Microsoft Digital Crimes Unit (DCU) has disrupted a spear-phishing operation linked to an Iranian threat actor tracked as Bohrium that targeted customers in the U.S., Middle East, and India.
Secureworks spotted a new campaign targeting vulnerable Elasticsearch databases to replace their indexes with a ransom note; a total ransom of $280,000 has been demanded. The attackers have used an automated script to parse unprotected databases, wipe out their data, and add the ransom note. Admins should set up MFA for authorized users and limit […]
Europol, along with law enforcement agencies from Finland, Austria, Belgium, Ireland, Spain, Sweden, Hungary, the U.S., the Netherlands, and Switzerland, took down FluBot’s infrastructure. The Dutch Police claimed to have disconnected 10,000 victims from the FluBot network and stopped over 6.5 million spam SMS from reaching potential victims.
The flaws affect Illumina Local Run Manager (LRM), which is used by sequencing instruments designed for clinical diagnostic use in the sequencing of a person’s DNA, testing for various genetic conditions, as well as research.
The SideWinder APT has launched more than 1,000 attacks while leveraging over 400 domains and subdomains, with additional stealth mechanisms. The threat group is maintaining a large C2 infrastructure comprising more than 400 domains and subdomains that were used to host malicious payloads and manage them. Please check IOCs that could help organizations update their […]
Sucuri, which has been tracking the same campaign since February 2019 under the name “NDSW/NDSX,” said that “the malware was one of the top infections” detected in 2021, accounting for more than 61,000 websites.