Europe’s data protection regime has reduced the number of apps available in Google Play by “a third,” increased costs, and reduced developer revenues, according to a study published Monday.
QNAP says only VS series NVR devices running QVR are impacted and that the issue was addressed with the release of QVR 5.1.6 build 20220401. The manufacturer encourages all users to update their systems to the latest release.
Over the past year, various vulnerabilities in Windows Print Spooler have been discovered. By abusing them, cybercriminals have been able to take control of servers and victims’ machines, even without special admin access.
The targets include both car manufacturers and car dealerships in Germany, and the threat actors have registered multiple lookalike domains for use in their operation by cloning legitimate sites of various organizations in that sector.
The company warned that the vulnerability enables an unauthenticated attacker on the BIG-IP system to run arbitrary system commands, create or delete files, or disable services.
Microsoft rolled out a new suite of new managed services aimed at the mid-market, betting that short-staffed organizations will need outside help to reduce bloating attack surfaces and mitigate an ongoing surge in malware attacks.
The malware can capture a wide range of information that ranges from taking screenshots to gathering passwords, cookies, and autofill data stored in Chromium-based browsers such as Google Chrome, Opera, Edge, Brave, Vivaldi, and Yandex, among others.
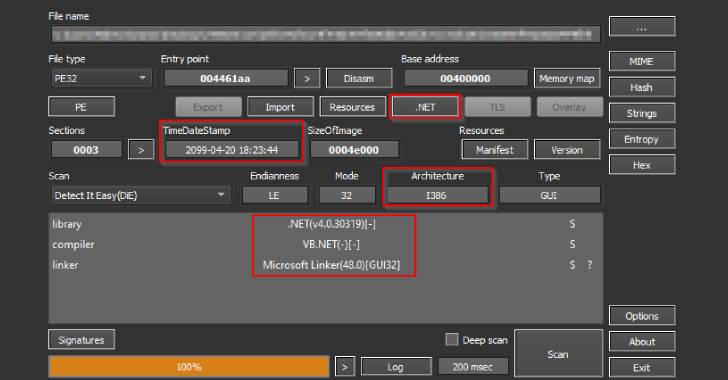
Based on the various techniques and modules (pen-testing suites, custom anti-detection wrappers, final stage trojans) used in the campaign, a researcher noted that the entire campaign “looks impressive.”
The City of London police provided Freedom of Information data to The Guardian which revealed that criminal gangs are increasingly combining physical threats with cyber-knowhow to part individuals with their virtual currency.
Proofpoint researchers have spotted low-volume Emotet activity that is much different from typical Emotet threat behaviors, highly likely that the group is testing a new threat before using it. The campaign was spotted between April 4 and April 19. The testing of different attack chains is most probably an attempt to evade detection and stay hidden.