A goodbye note posted to the school’s website said that it survived both World Wars, the Spanish flu and the Great Depression, but was unable to handle the combination of the Covid pandemic and a severe ransomware attack in December last year.
The U.S. Department of Transportation’s Pipeline and Hazardous Materials Safety Administration (PHMSA) found management failings and has issued a Notice of Probable Violation and Proposed Compliance Order to Colonial Pipeline Company.
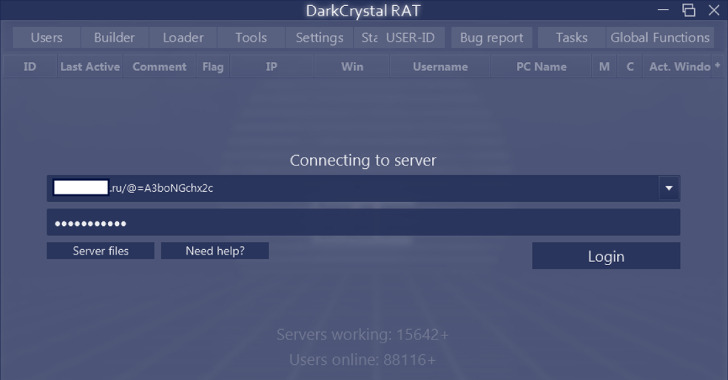
Cybersecurity researchers have shed light on an actively maintained remote access trojan called DCRa that’s offered on sale for “dirt cheap” prices, making it accessible to professional cybercriminal groups and novice actors alike.
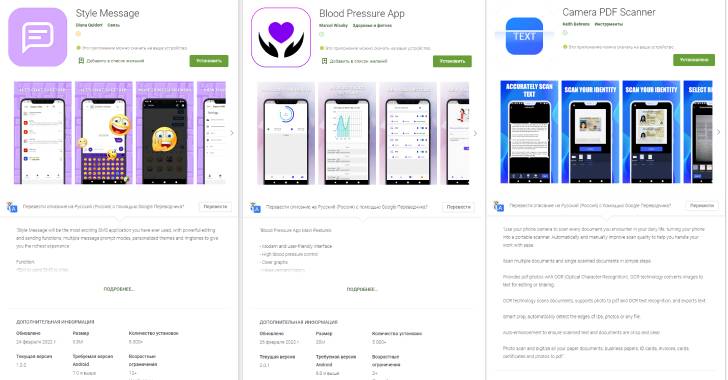
Joker, a repeat offender, refers to a class of harmful apps that are used for billing and SMS fraud, while also performing a number of actions of a malicious hacker’s choice, such as stealing text messages, contact lists, and device information.
Costa Rican President Rodrigo Chaves has declared a national emergency following cyber attacks from the Conti ransomware group on multiple government bodies. Conti reportedly published most of the 672 GB data dump.
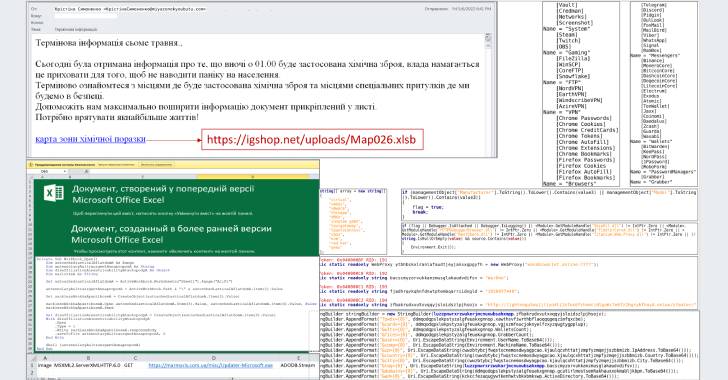
The attack, which requires potential victims to enable macros after opening the document, works by downloading and executing an .EXE file that is retrieved from compromised web resources, CERT-UA detailed.
This service supplies subscribers with a skimmer script, deployment instructions, and a campaign management panel, which is everything a threat actor needs to launch their own credit card stealing campaign.
The site offers “tweaked apps”, apparently available with a single click and requiring “no jailbreak, no root.” There’s an OnlyFans Premium, Netflix Premium, a Pokemon Go Spoofer Injector, and many more.
The United States state department has offered a reward of up to $15 million for information on the Russia-based Conti ransomware group, which has been blamed for cyber extortion attacks worldwide.
A threat researcher from Trellix claimed that APT38 operators (aka Unit 180 of North Korea) have used Beaf, ZZZZ, ChiChi, and PXJ ransomware strains to extort some of their victims.