Potentially exposed data included names, social security numbers, drivers’ license or state identification numbers, dates of birth, financial account information, and medical treatment information among other confidential information.
According to the report released by the researchers at Sucuri, vulnerable plugins and extensions “account for far more website compromises than out-of-date, core CMS files”.
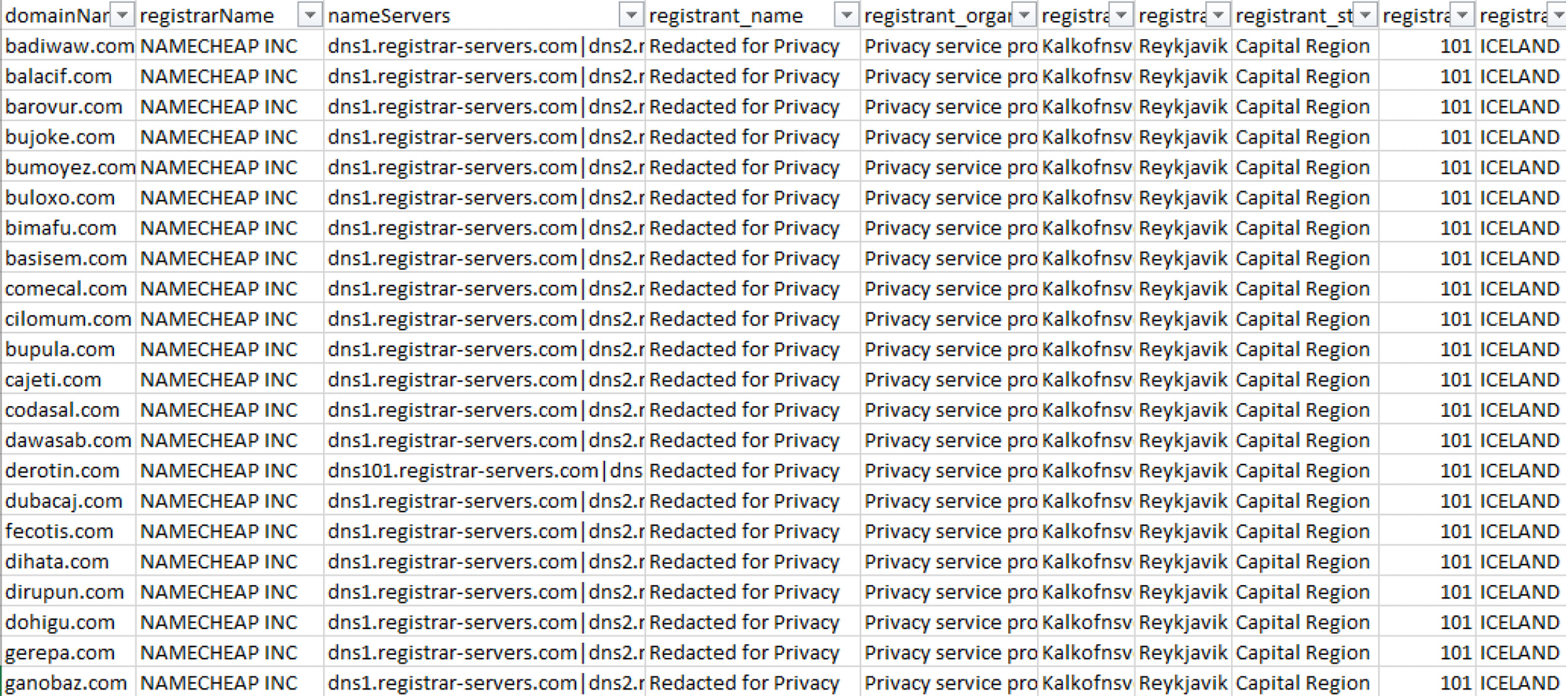
A majority of the domain IoCs of Conti ransomware share the same lexical features in that they don’t seem to be English words and follow a succession of consonant-vowel patterns.
GitHub shared the timeline of breaches in April 2022, this timeline encompasses the information related to when a threat actor gained access and stole private repositories belonging to dozens of organizations.
Library lending app Onleihe announced problems lending several media formats offered on the platform, like audio, video, and e-book files, after a cyberattack targeted their vendor.
A mass phishing campaign is targeting Windows PCs and aims to deliver malware that can steal usernames, passwords, credit card details, and the contents of cryptocurrency wallets.
While Redis statically links the Lua Library, some Debian/Ubuntu packages dynamically link it, leading to a sandbox escape that can be exploited to achieve remote code execution.
PeckShield said the attacker stole about $13.4 million worth of cryptocurrency but noted that the platform’s actual losses may be larger. CertiK put the losses at 5,446 ETH, or about $15.7 million.
Websites containing a recently vulnerable plugin or other extension are most likely to be caught up in malware campaigns. Default configurations of popular website software applications remain a serious liability, according to Sucuri.
The ease with which one can purchase a rogue device, thanks to their accessibility and low cost, exacerbates the risk (many costing less than $100 on sites such as AliExpress).