New B1txor20 botnet is actively exploiting Log4j flaws in Linux systems to create a bot army that helps hackers install rootkits and steal sensitive records. The bot sends the stolen information, results of any command execution, or any other information to its C2 server in form of a DNS request. The malware possesses many additional features […]
Security experts linked the activities of Shamoon APT with those behind Kwapirs malware. They said both could be from the same group as they have been collaborating, sharing updates, techniques, and codes for years. Organizations should be ready with countermeasures including reliable anti-malware solutions to thwart such threats.
Researchers spotted the third wiper malware in use against Ukrainian organizations, which destroys user data and partition information from attached drives while also reporting a new phishing attack. The Ukrainian agency has linked the recent activity with the UAC-0056 group with medium confidence.
Botnet activity that drew loud warnings last month from U.S. and U.K. cybersecurity agencies has expanded to a second type of hardware, according to researchers at Trend Micro.
Newer versions of the ‘node-ipc’ package began deleting all data and overwriting all files on developer’s machines, in addition to creating new text files with “peace” messages.
The Lapsus$ cyber-crime gang, believed to be based in Brazil, until recently was best known for attacks on that country’s Ministry of Health and Portuguese media outlets SIC Noticias and Expresso.
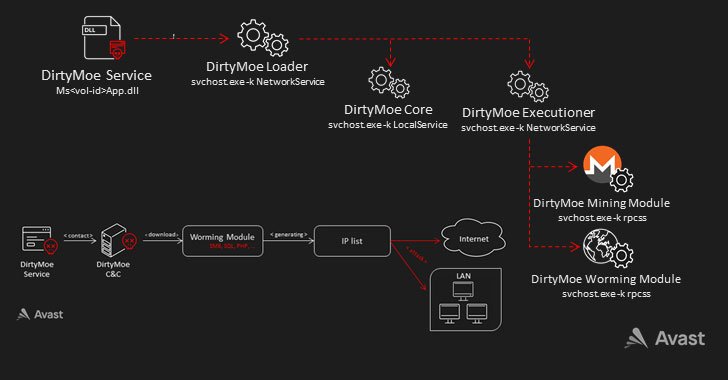
The malware known as DirtyMoe has gained new worm-like propagation capabilities that allow it to expand its reach without requiring any user interaction, the latest research has found.
The Security Service of Ukraine (SBU) said it has detained a “hacker” who offered technical assistance to the invading Russian troops by providing mobile communication services inside the Ukrainian territory.
The backdoor infecting all sites is a 2015 Google search SEO-poisoning tool implanted on the wp-config.php to fetch spam link templates from the C2 that are used to inject malicious pages into search results.
Recently, the BazarBackdoor malware was observed spreading via corporate website contact forms rather than its typical phishing email attack chain target firms. To avoid any possible security flag, the attackers use file-sharing services TransferNow and WeTransfer to send malicious files. Website admins are suggested to stay alert whenever receiving suspicious emails from unknown sources.