As per the Quarterly Threat Trends & Intelligence Report by PhishLabs, social media threats increased by 103% from January to December 2021. In December, organizations witnessed an average of 68 attacks per month.
Tracked as CVE-2022-23131 and CVE-2022-23134, the two flaws could be exploited to bypass authentication and gain admin privileges, which could then allow an attacker to execute arbitrary commands.
Three new threat groups targeting firms in the industrial sector have appeared but over half of all attacks are the work of only two known cybercriminal outfits, researchers say.
Similarities have been unearthed between the Dridex malware and a ransomware called Entropy, suggesting that the operators are continuing to rebrand their extortion operations under a different name.
Samsung failed to implement Keymaster TA properly in Galaxy S series phones, meaning one could launch an Initialization Vector reuse attack to obtain the keys from the hardware-protected key blobs.
Security experts spotted a new version of the CryptBot infostealer that is offering free download versions of cracked games and pro-grade software. Its operators are using search engine optimization to rank up the distribution sites to display them at top of Google search results, allowing increased chances of infection. For users, avoiding downloading pirated software […]
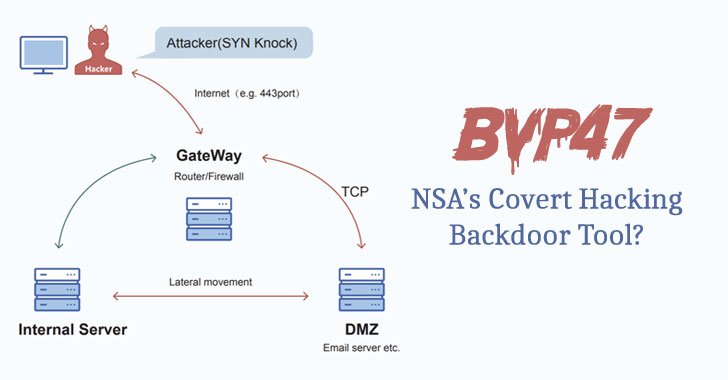
Dubbed “Bvp47” owing to numerous references to the string “Bvp” and the numerical value “0x47” used in the encryption algorithm, the backdoor was extracted from Linux systems in 2013.
A new banking trojan called Xenomorph was found distributing via Google Play Store in the form of fake performance-boosting apps, targeting European banks. It comes with a modular engine that abuses accessibility services, which may allow advanced capabilities. Experts recommend using an anti-malware app in smartphones and monitoring app behavior after installations.
Source code for an Airtag clone was published online by Positive Security, which said its tags “successfully tracked an iPhone user… for over five days without triggering a tracking notification.”
IBM researchers say that phishing remains the most common attack vector for cyberattacks but there has also been a 33% increase in the use of vulnerabilities against unpatched systems.