Researchers from Inky detailed a series of phishing attacks in which the sender address on most of the emails appeared to come from no-reply@dol.gov, the real domain for the Department of Labor.
Researchers from AppCheck announced they had found two separate vulnerabilities, an application URL overwrite (CVE-2022-22690) and a persistent password reset bug (CVE-2022-22691).
VirusTotal, the popular online service for analyzing suspicious files, URLs and IP addresses, can be used to collect credentials stolen by malware, researchers at SafeBreach have found.
The cyberattack was attributed to the financially-motivated advanced persistent threat (APT) actor FIN11. Operating out of Russia, FIN11 is believed to be a TA505 spin-off.
Fortinet discovered a new RedLine info-stealer campaign impersonating the COVID-19 Omicron stat counter app as a lure to steal data. The victims of the attack campaign are reportedly distributed across 12 countries. Security teams are advised to deploy a reliable anti-malware solution, encrypt important data, and use a network firewall, to say the least, to […]
A relatively inactive TellYouThePass ransomware has re-emerged as a Golang-compiled malware, making it easier for threat actors to target a wide range of operating systems, including macOS and Linux. Hackers demand 0.05 Bitcoin, presently converting to around $2,150, for the decryption tool. TellYouThePass is financially motivated ransomware that was first seen in 2019.
The attacks started on January 13 – around the same time when more than 70 government websites were defaced by gangs reportedly linked to Russian secret services.
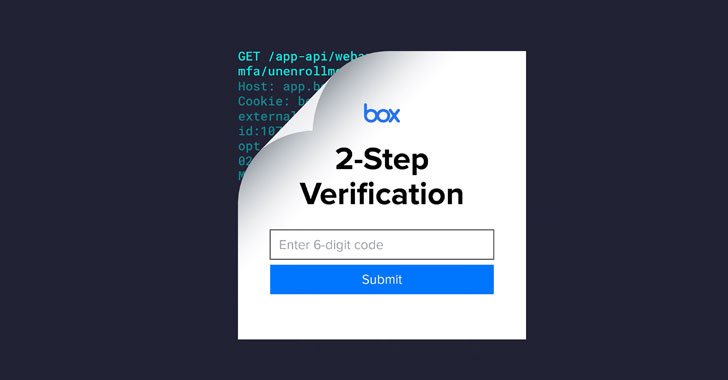
Cybersecurity researchers have disclosed details of a now-patched bug in Box’s multi-factor authentication (MFA) mechanism that could be abused to completely sidestep SMS-based login verification.
MuddyWater, aka Seedworm, is an Iranian cyberespionage threat actor that primarily targets the UAE, Saudi Arabia, Israel, Iraq, and other Middle Eastern nations, as well as some European and North American countries.
The company addressed the data breach on its portal and sought to assure its customers that no sensitive information was compromised. On Monday, it was reported that the company’s database was hacked.