Based on the activity clusters, researchers have detected two diverse activity clusters, named UNC3004 and UNC2652. Possibly the Nobelium group (aka UNC2452) is cooperating with these two hacking groups.
Botnet operator MANGA was spotted abusing a recently disclosed vulnerability to hijack TP-Link routers and add them to their network of hacked devices. Attackers started exploiting the flaw just two weeks after TP-Link released the firmware update. Experts recommend always updating devices regularly and changing the default password with strong ones.
Researchers unearth the first professional ransomware variant written in Rust dubbed BlackCat. It can target Windows, Linux, and VMWare ESXi systems. The threat group uses a double extortion model and looks for partners to whom it offers a huge 80%–90% ransom cut. As per claims, the author of BlackCat ransomware was previously involved with REvil […]
Researchers from Accenture Security have been tracking a group that calls itself “Karakurt,” which means “black wolf” in Turkish and is the name of a venomous spider found in eastern Europe and Siberia.
Security researchers have uncovered details about the first Rust-language-based ransomware strain spotted in the wild that has already amassed “some victims from different countries” since its launch last month.
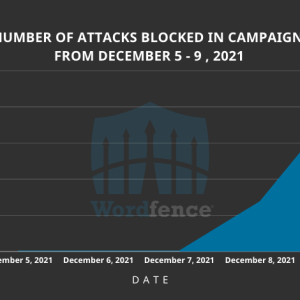
As many as 1.6 million WordPress sites have been targeted by an active large-scale attack campaign originating from 16,000 IP addresses by exploiting weaknesses in four plugins and 15 Epsilon Framework themes.
Wordfence researchers spotted a massive wave of attacks in the days that are targeting over 1.6 million WordPress sites from 16,000 IPs via four different plugins and several Epsilon Framework themes.
Qakbot has in the past year started delivering ransomware and this new business model is making it harder for network defenders to detect what is and isn’t a Qakbot attack.
Vulnerabilities in Microsoft and others’ popular OAuth2.0 implementations lead to redirection attacks that bypass most phishing detection solutions and email security solutions.
If exploited, the most severe of these security bugs could allow attackers to execute arbitrary code within the context of the vulnerable application, which could lead to full system compromise.