Fail2Ban is an open-source tool that monitors log files and blocks IP addresses that exhibit repeated failed login attempts. It does this by updating firewall rules to reject new connections from those IP addresses for a configurable amount of time.
Security researchers have revealed a series of criminal campaigns that exploit cloud storage services such as Amazon S3, Google Cloud Storage, Backblaze B2 and IBM Cloud Object Storage.
“This guidance helps organizations disrupt malicious cyber activity by applying granular access control and visibility to applications and workloads in modern network environments,” said Dave Luber, director of cybersecurity at NSA.
Forcepoint X-Labs has recently observed a significant number of phishing email instances in their telemetry targeting various government departments in APAC that masquerade as PDF viewer login pages.
“Through ongoing monitoring and collaboration with cyber authorities, we identified attempts to replace our Viewer 8.3.7 software with a compromised file,” the company said in a statement on Thursday.
National Cyber Director Harry Coker Jr. said the administration is taking actions to strengthen key critical infrastructure sectors, including healthcare and water utilities, and will pursue additional steps to fight ransomware and boost resilience.
The threat actors demonstrate increased caution in selecting their targets, broadening their reconnaissance efforts, and adopting Cobalt Strike Beacon over custom backdoors.
Effective, updated policies are foundational to an organization’s cybersecurity strategy in this new era of AI-driven attacks. CISOs must proactively adapt their email security approach to protect against the latest social engineering threats.
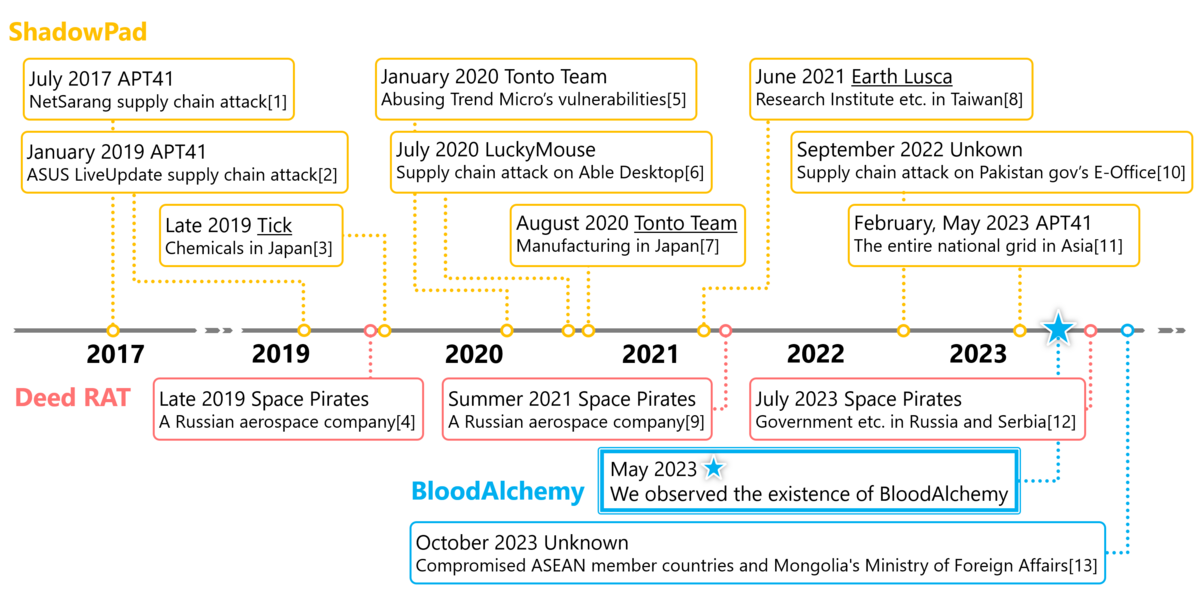
BLOODALCHEMY is an updated version of Deed RAT, which is believed to be a successor to ShadowPad malware. It has been used in attacks targeting government organizations in Southern and Southeastern Asia.
“Rather than scam or phish everyday people directly for gift card-based payments, Storm-0539 infiltrates large retailers and fraudulently issues gift card codes to themselves, virtually printing their own money,” Microsoft’s Vasu Jakkal explained.