This year, Microsoft observed the actors scanning for many vulnerabilities, including those targeting Fortinet FortiOS SSL VPN, Microsoft Exchange Servers vulnerable to ProxyShell, and more.
The header smuggling method by Daniel Thatcher creates a mutation in a header request designed to be sent through to backend infrastructure without being processed by a trusted frontend service.
By combining the two services, Team Cymru will be able to inform its customers on both the evolving threats and where they might strike against Amplicy-detected perimeter weaknesses.
Scam Spotter predicts that 2021 will be a bumper year for gift card scamming as holiday shoppers seek to overcome product shortages and supply-chain issues by choosing gift cards over other presents.
More than 125 people and businesses associated with large TikTok accounts based around the world were targeted as part of a recent phishing campaign, according to research published Tuesday.
Out of the two disclosed flaws, the first one concerns the leak of names of private npm packages on the npmjs.com’s ‘replica’ server—feeds from which are consumed by third-party services.
Twelve of these vulnerabilities could allow a malicious user to manipulate the Web Manager in a way — for example, overflowing a fixed-size buffer — that would allow them to execute arbitrary code.
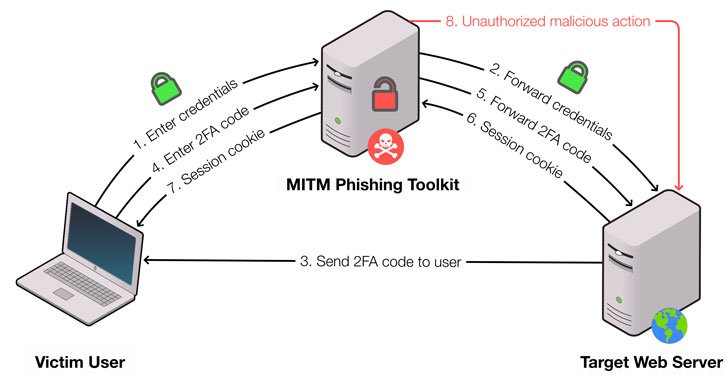
No fewer than 1,220 Man-in-the-Middle (MitM) phishing websites have been discovered as targeting popular online services to hijack users’ credentials and carry out further follow-on attacks.
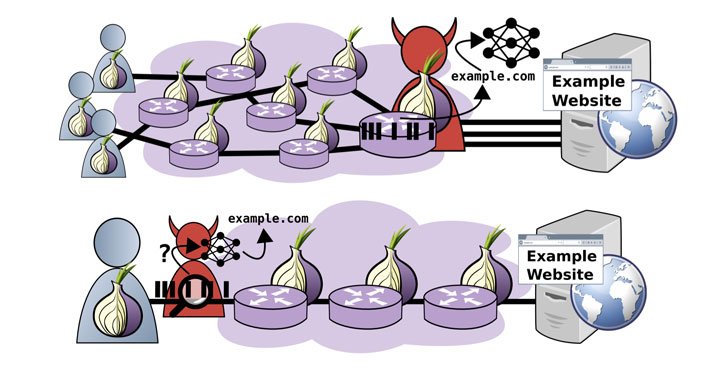
A new analysis of website fingerprinting (WF) attacks aimed at the Tor web browser has revealed that it’s possible for an adversary to glean a website frequented by a victim.
Current Department of Homeland Security employees are not obligated to join the department’s new Cyber Talent Management System, but they may want to consider it, according to senior DHS officials.