An attorney discovered that the mobile ads she saw were reflecting her recent library audiobook borrowing habits, raising concerns about the privacy of library patron data and the potential for targeted advertising based on that information.
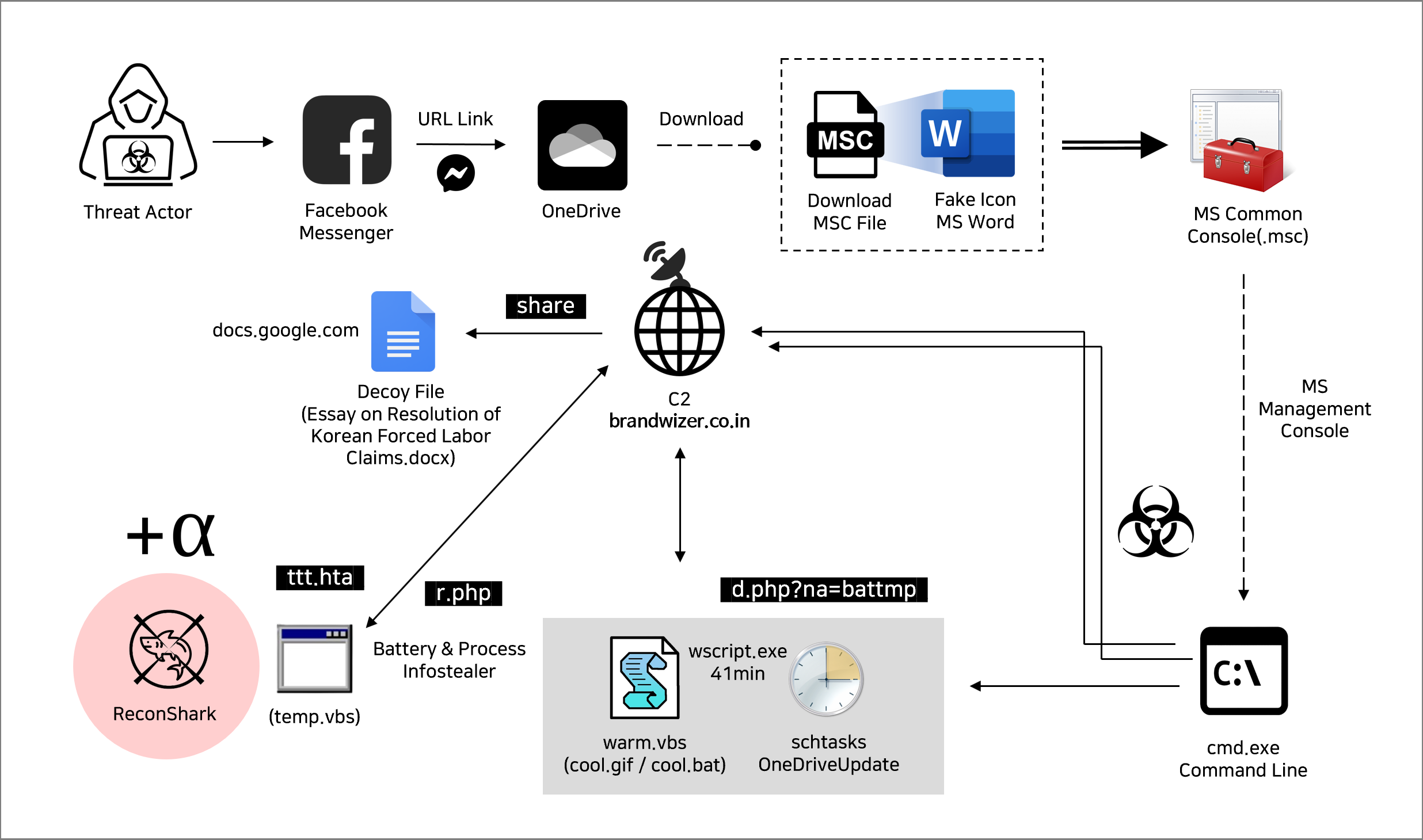
Researchers at Genians Security Center (GSC) identified the North Korea-linked Kimsuky APT group targeting victims via Facebook Messenger, using fake accounts posing as South Korean officials to deliver malware.
Cybercriminals’ new tactics led to a 64% increase in ransomware claims in 2023, driven by a 415% rise in “indirect” incidents and remote access vulnerabilities, pressuring more victims to pay ransoms, according to At-Bay.
Two Chinese nationals have been indicted for their alleged involvement in a multimillion-dollar “pig butchering” investment fraud scheme, where they laundered over $73 million through US financial institutions and cryptocurrency wallets.
The enterprise attack surface is rapidly expanding due to the convergence of IT and OT systems, leading to a large number of ICS assets being exposed to the public internet and creating new vulnerabilities that security teams struggle to manage.
The SEC has approved new regulations that require broker-dealers and investment firms to notify their clients within 30 days of detecting a data breach, in an effort to modernize and enhance the protection of consumers’ financial data.
A critical vulnerability in the Jinja2 template rendering Python tool used by the llama_cpp_python package for integrating AI models can allow hackers to execute arbitrary code, putting systems and data at risk.
The judge said the plaintiffs did not show an “administratively feasible” way for the court to determine whether a particular individual is a class member without extensive and individualized fact-finding.
Researchers have observed a surge in email phishing campaigns delivering Latrodectus, a new malware loader believed to be the successor to the IcedID malware, which is capable of deploying additional payloads such as QakBot, DarkGate, and PikaBot.
Adequate IAM policies are essential for incident management tooling to ensure the right people can quickly address issues without being blocked. Authentication verifies a person’s identity, while authorization manages permissions and access levels.