Google last week pledged $1 million in financial support to the Secure Open Source (SOS) rewards program run by the Linux Foundation. The pilot program financially rewards developers who help improve the security of critical open-source projects.
It’s the time of year when we need to remember and reinvigorate our efforts to achieve greater awareness of the threats and risks posed by the malicious cyber activity of sophisticated threat actors.
One of the newer techniques for BEC scams integrates spear phishing, custom webpages, and the complex cloud single sign-on ecosystem to trick users into unwittingly divulging their credentials.
Arctic Wolf, a managed cybersecurity company that offers a “security operations-as-a-concierge” service, has acquired Habitu8, a security training content platform for an undisclosed amount.
Superhero-based passwords are increasingly showing up in datasets of breached information, according to a new blog post from Mozilla. Mozilla used data from haveibeenpwned.com to figure out the most common passwords found in breached datasets.
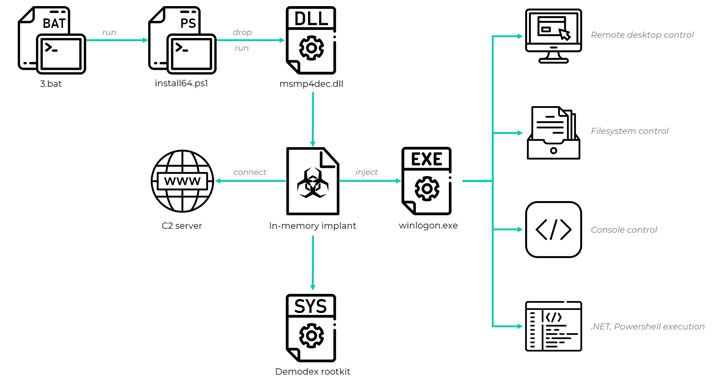
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems.
FluBot attacks have commonly come in the form of text messages which claim the recipient has missed a delivery, asking them to click a link to install an app to organize a redelivery. This app installs the malware.
Hackers stole from the accounts of at least 6,000 customers of Coinbase Global Inc, according to a breach notification letter sent by the cryptocurrency exchange to affected customers.
The topics of the meeting, President Biden said, will include combating cybercrime, improving law enforcement collaboration, stemming the illicit use of cryptocurrency, building trusted 5G technology and better securing supply chains.
The Flubot malware has switched to a new and likely more effective lure to compromise Android devices, now trying to trick its victims into infecting themselves with the help of fake security updates.