IBM Security X-Force researchers continue to track the infrastructure and activity of a suspected Iranian threat group ITG18. This group’s TTPs overlap with Charming Kitten, Phosphorus, and TA453.
A recently discovered Prometheus traffic distribution system is helping malware and cybercrime gangs distribute their malicious payloads to unsuspecting users using hacked websites.
The tool, which scrapes both the clear web and dark web for exposed credentials, is designed for use by workers in security operations, incident response, threat intelligence, and pen testing roles.
Discovered by Evan Grant of Tenable, the critical path traversal flaw is tracked as CVE-2021–20090, with a CVSS of 9.8, and is exploitable by unauthenticated, remote attackers.
The NSA warned all federal employees, leading defense contractors, and civilian personnel that hackers could take advantage of the public Wi-Fi in coffee shops, airports, and hotel rooms.
The misconfigured S3 bucket compromised the details of over 300,000 customers from various Reindeer clients. Patrón was the client firm with the most customers’ PIIs exposed.
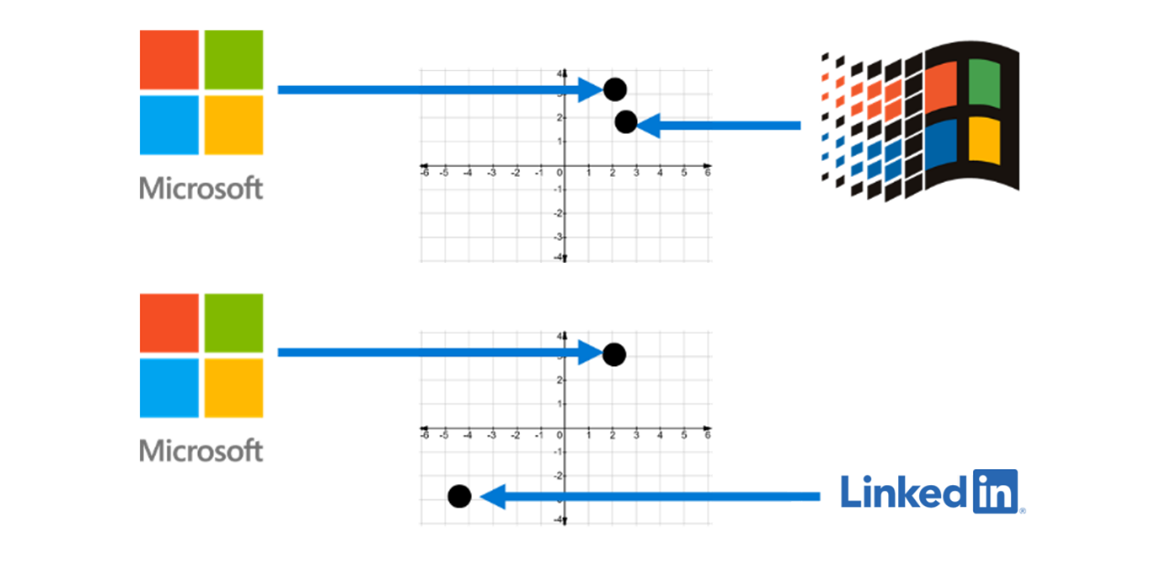
Using a combination of ML techniques, Microsoft developed a detection system that outperforms all visual fingerprint-based benchmarks on all metrics while maintaining a 90% hit rate.
These backdoors are intentionally hidden from public view, rendering any remote or external scanners futile, and the dynamic nature of these backdoors makes signature-based detection less reliable.
A security researcher exploited IoT flaws that allowed him to hijack the controls for any room at the hotel to mess with its lights, ventilation, and the beds in each room that convert to a couch.
The Biden administration backed away from the idea of banning ransomware payments after meetings with the private sector and cybersecurity experts, a top cybersecurity official said Wednesday.