Russian cyberattacks are being deployed with new techniques – including exploiting vulnerabilities like the recent Microsoft Exchange zero-days – as its hackers continue to target governments, organizations, and energy providers around the world.
A cyberattack forced the shutdown of one of the largest pipelines in the United States, in what appeared to be a significant attempt to disrupt vulnerable energy infrastructure.
U.S. intelligence agencies have begun a review of supply chain risks emanating from Russia in light of the far-reaching hacking campaign that exploited software made by SolarWinds and other vendors, a top Justice Department official said.
Foxit Software, the company behind the highly popular Foxit Reader, has published security updates to fix a high severity remote code execution (RCE) vulnerability affecting the PDF reader.
Russian spies from APT29 responded to Western agencies outing their tactics by adopting a red-teaming tool to blend into targets’ networks as a legitimate pentesting exercise.
The 7GB trove contained over 13 million records including the email addresses and WhatsApp/Telegram phone numbers of vendor contacts, plus email addresses, surnames, PayPal account details and Amazon account profiles of reviewers.
An investigation revealed that certain files were accessed without permission, including first and last names, dates of birth, prescription information, and medical record numbers.
Microsoft detected a large-scale business email compromise (BEC) campaign that targeted more than 120 organizations using typo-squatted domains registered a few days before the attacks started.
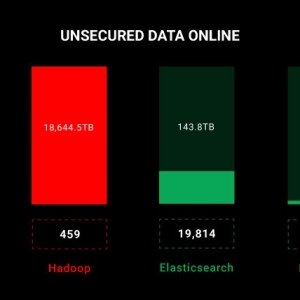
CyberNews researchers found more than 29,000 unprotected databases worldwide that are still publicly accessible, leaving close to 19,000 terabytes of data exposed to anyone, including threat actors.
The main issues affecting routers supplied by ISPs such as Virgin, EE, Sky, TalkTalk, and Vodafone were weak default passwords, local network vulnerabilities, and the lack of firmware updates to patch security loopholes.