Researchers Uncover Chinese Nation State Hackers’ Deceptive Attack Strategies
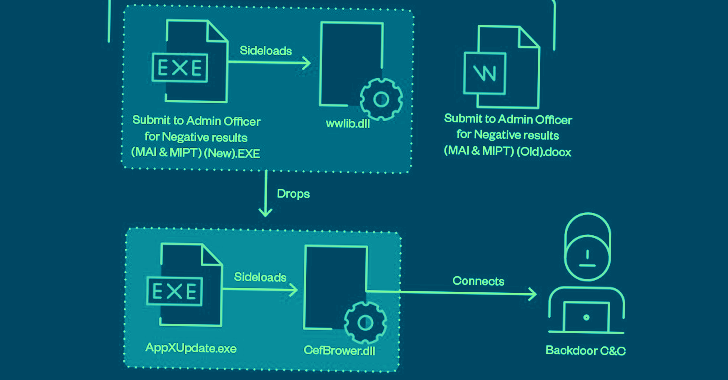
Attack chains mounted by the group commence with a spear-phishing email to deploy a wide range of tools for backdoor access, command-and-control (C2), and data exfiltration.