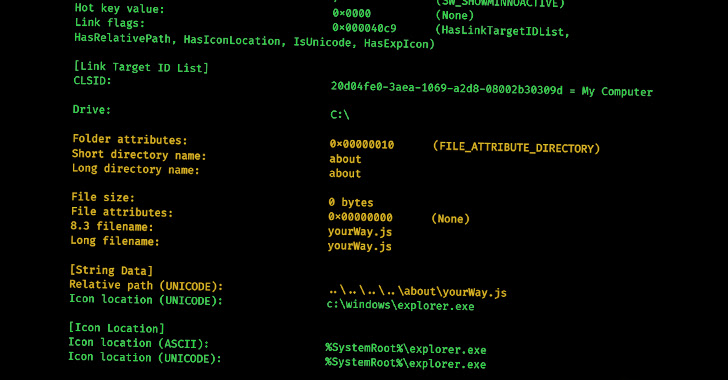
New Research Delves into the World of Malicious LNK Files and Hackers Behind Them
A recent study has shown that it is possible to identify relationships between different threat actors by analyzing the metadata of malicious LNK files, uncovering information such as the specific tools and techniques used by different groups.