Cyber X
Breach Automation Platform
Continuous Security Validation Across the Full Kill Chain
Cymulate’s breach and attack simulation platform is used by security teams to determine their security gaps within seconds and remediate them.
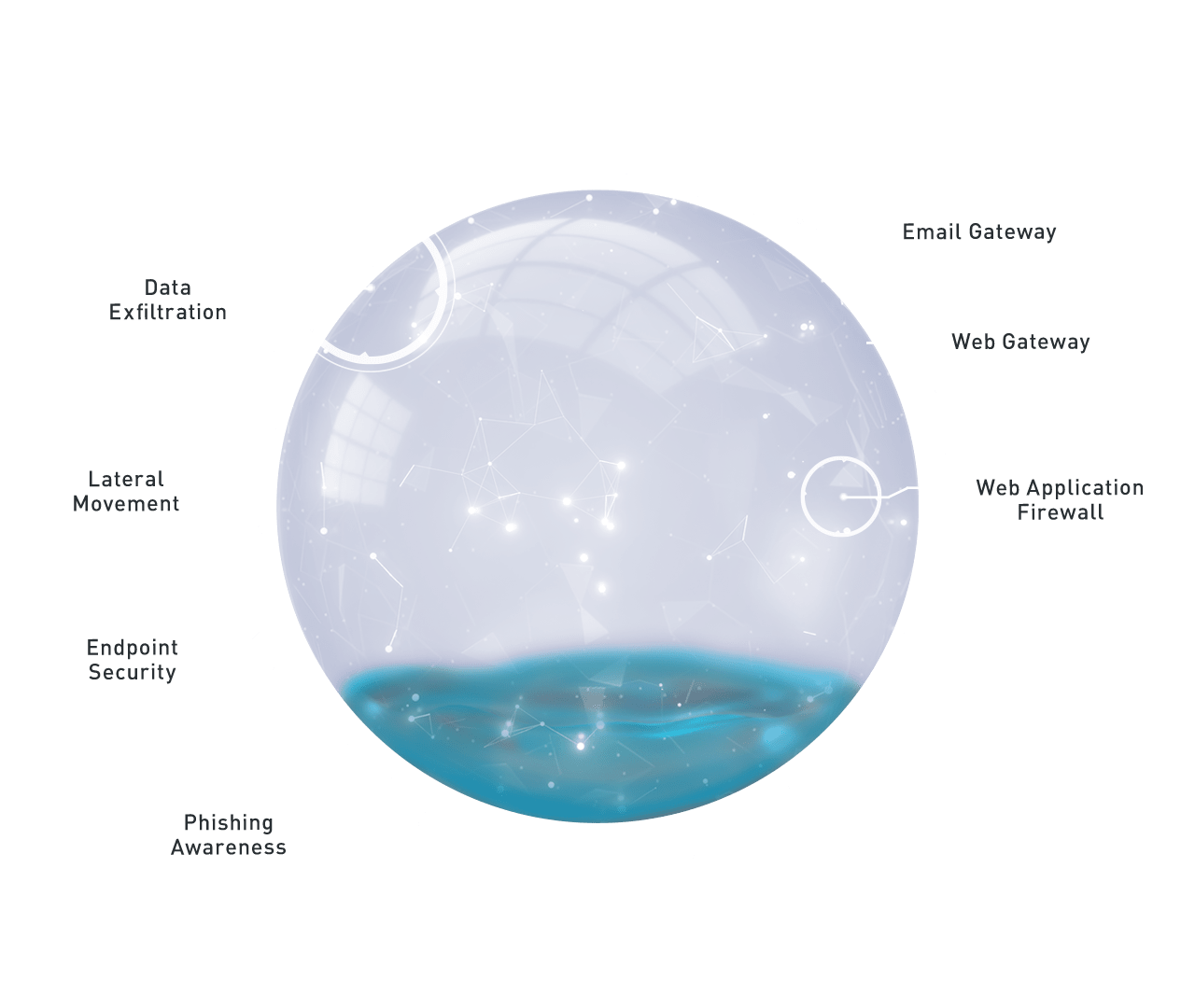
Cymulate Breach and Attack Simulation
Security leaders should engage in a continuous security posture assessment, applied to its highest risk threat vectors
0
0
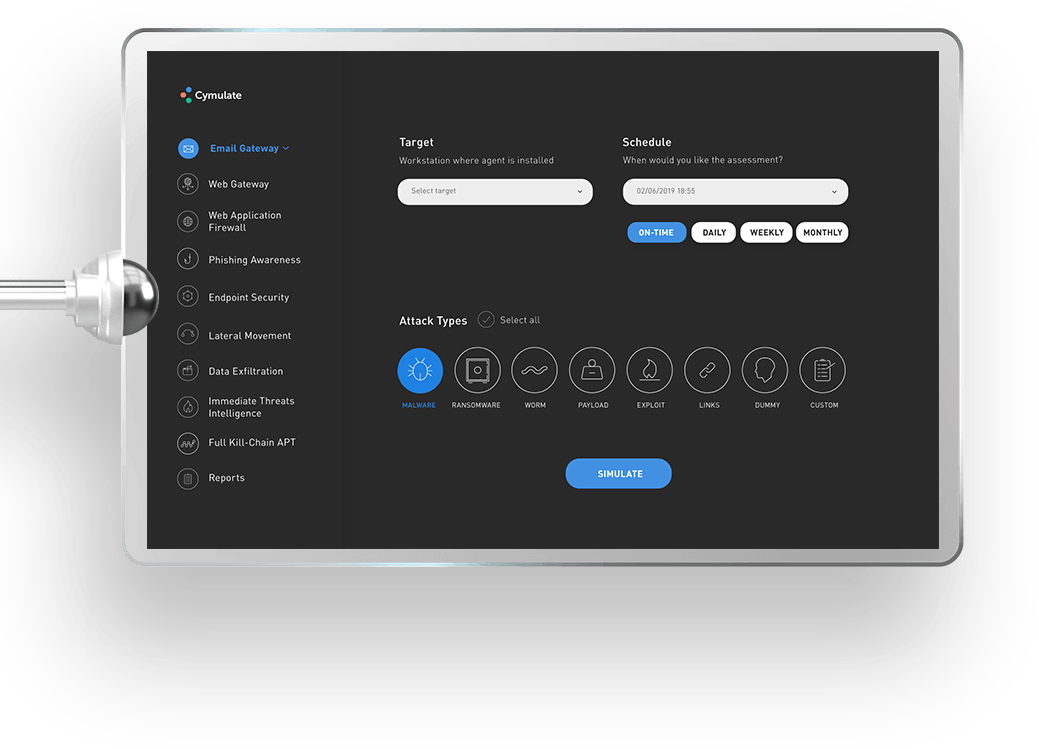
Simulate
Simulate attacks across any vector
0
1
Evaluate
Know where your company is exposed
0
0
Remediate
Fix your security gaps
Monitor your security posture continuously
Complete Attack Vector Coverage
Cymulate’s full kill chain attack vectors simulations analyze all areas of your organization including for example web apps, email, phishing, and endpoints, so no threats slip through the cracks.