The two founders of a cryptocurrency mixing service that allegedly obfuscated the origins of at least $100 million in criminal proceeds have been arrested, the Department of Justice announced Wednesday.
Flowon developer Progress Software first alerted about the flaw on April 4, warning that it impacts versions of the product v12.x and v11.x. The company urged system admins to upgrade to the latest releases, v12.3.4 and 11.1.14.
On Wednesday, the Cybersecurity and Infrastructure Security Agency (CISA) added two Cisco product vulnerabilities — CVE-2024-20353 and CVE-2024-20359 — as well as one vulnerability affecting popular file transfer tool CrushFTP.
Google announced it is updating the client-side encryption mechanism for Google Meet to allow external participants, including those without Google accounts, to join encrypted calls.
Chinese and Russian hackers have turned their focus to edge devices — like VPN appliances, firewalls, routers and Internet of Things (IoT) tools — amid a startling increase in espionage attacks, according to Google security firm Mandiant.
A security researcher discovered vulnerabilities in the popular phone-tracking app iSharing, which has over 35 million users. The bugs allowed a user to access others’ precise coordinates, even if the user wasn’t actively sharing their location data.
Researchers observed a malicious ad campaign targeting Facebook users via Google search. The ad, which appears at the top of Google search results for the keyword “Facebook,” redirects users to a scam page.
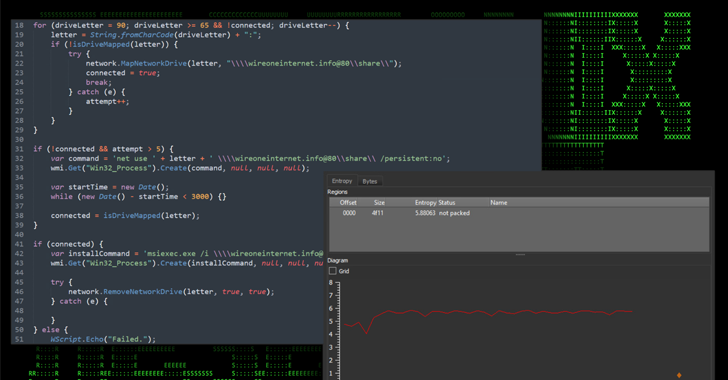
“SSLoad is designed to stealthily infiltrate systems, gather sensitive information and transmit its findings back to its operators,” security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
An Iranian state-sponsored hacking group successfully infiltrated hundreds of thousands of employee accounts at US companies and government agencies, including the US Treasury and State Department, as part of a five-year cyber espionage campaign.
The vulnerabilities could be exploited to “completely reveal the contents of users’ keystrokes in transit,” researchers Jeffrey Knockel, Mona Wang, and Zoë Reichert said.