Threat actors have been using scanning methods to pinpoint vulnerabilities in networks or systems for a very long time. Some scanning attacks originate from benign networks likely driven by malware on infected machines.
The threat actor behind the fake e-shop campaign leverages tools such as the open-source string obfuscator “Paranoid” and the Janus WebRTC module, showcasing a deep understanding of technological intricacies to evade detection and amplify impact.
Martin Schobert at Swiss security firm Pentagrid discovered that an attacker could input a series of six consecutive dashes (——) in place of a booking reference number and the terminal would return an extensive list of room details.
Hackers are using Facebook advertisements and hijacked pages to promote fake Artificial Intelligence services, such as MidJourney, OpenAI’s SORA and ChatGPT-5, and DALL-E, to infect unsuspecting users with password-stealing malware.
Two China-based Android app developers are being sued by Google for an alleged scam targeting 100,000 users worldwide through fake cryptocurrency and other investment apps.
One security researcher investigating AI-hallucinated libraries said late last month that he found chatbots calling for a nonexistent Python package dubbed “huggingface-cli.”
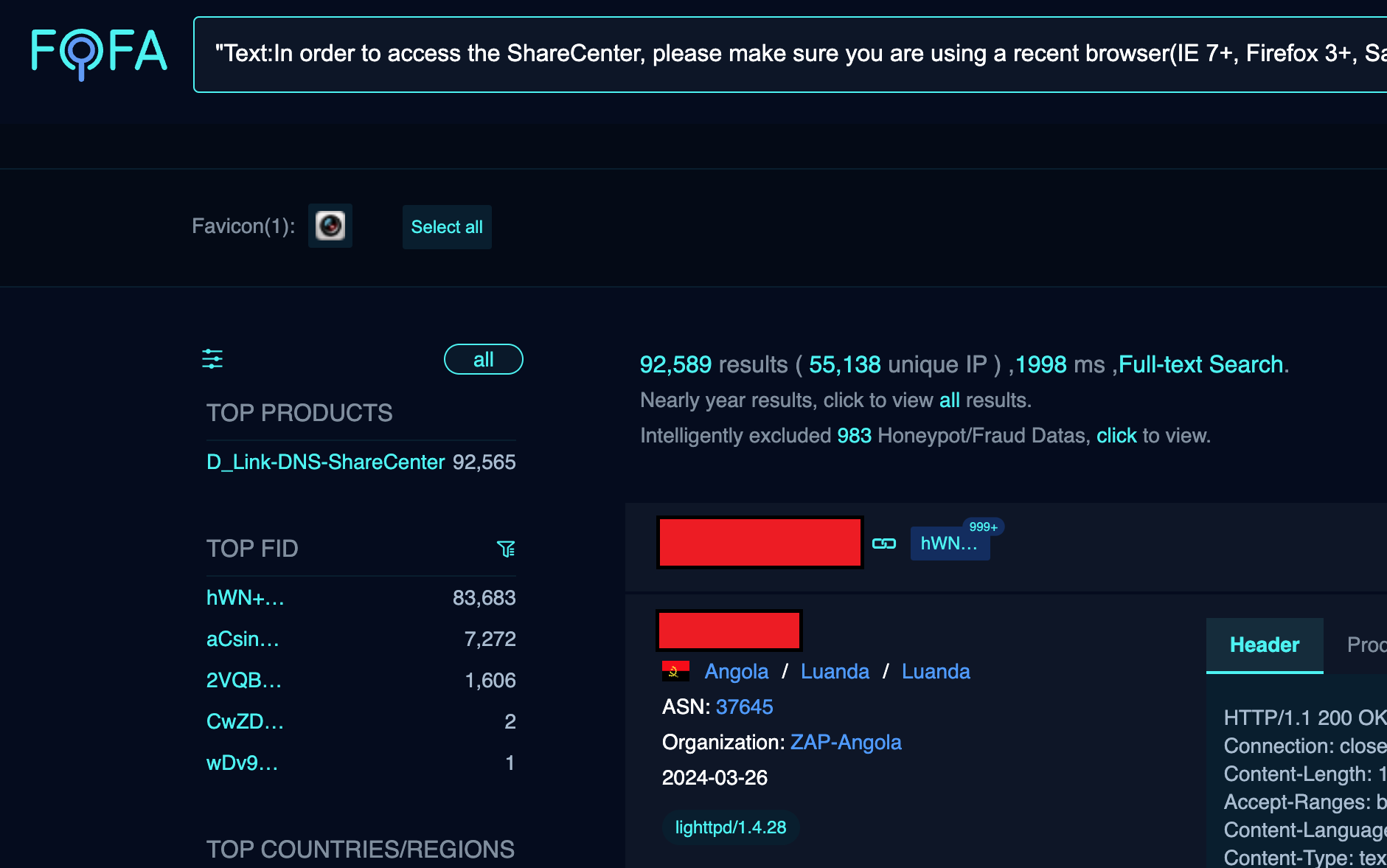
A researcher who goes online with the moniker ‘Netsecfish’ disclosed a new arbitrary command injection and hardcoded backdoor flaw, tracked as CVE-2024-3273, that impacts multiple end-of-life D-Link NAS device models.
The U.S. Chamber of Commerce and multiple industry leaders are calling for a month-long extension of the 60-day comment period for a new incident reporting rule being issued by the top cybersecurity agency in the U.S.
According to Silicon Angle, this significant injection of capital is spearheaded by Altimeter Capital Management LP, with notable participation from Point72 Ventures LLC, marking a new milestone for the company founded in 2020.
A police investigation has been launched after MPs were apparently targeted in a “spear-phishing” attack, in what security experts believe could be an attempt to compromise the UK Parliament.