In an update on Monday, Oxfam Australia said it had found “supporter’s information on one of its databases was unlawfully accessed by an external party on 20 January 2021”.
Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to HAFNIUM, a group assessed to be state-sponsored and operating out of China, based on observed victimology, tactics, and procedures.
Malaysia Airlines has suffered a data security “incident” that compromised personal information belonging to some of its members. The breach is purported to involve a third-party IT service provider.
A Chinese state-backed hacking group has in recent weeks targeted the IT systems of two Indian vaccine makers whose coronavirus shots are being used in the country, Cyfirma told Reuters.
When the most advanced hackers do succeed in breaking in, something strange happens: Apple’s extraordinary defenses end up protecting the attackers themselves instead of keeping them out.
Ticketcounter, a Dutch e-Ticketing platform, has suffered a data breach after a user database containing 1.9 million unique email addresses was stolen from an unsecured staging server.
A ransomware attack last fall caused $67 million in pre-tax losses at Universal Health Services, the U.S. health care provider has revealed, illustrating the financial toll caused by hackers.
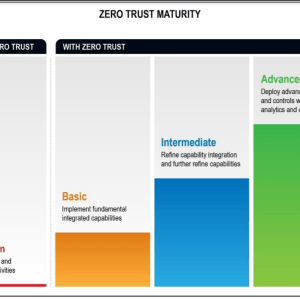
This model eliminates implicit trust in any entities inside or outside the perimeter of an organization, instead, it recommends implementing authorization and authentication for all processes.
The said password “solarwinds123” was originally believed to have been publicly accessible via a GitHub repository since June 17, 2018, before the misconfiguration was addressed on November 22, 2019.
A key lawmaker highlighted a profit motive for “basic” cybersecurity as problematic, following an exchange with Microsoft President Brad Smith at a Congressional hearing Friday.