The integration of Atom Security’s technology into Mend.io’s product line is expected to enhance coverage and reduce the number of irrelevant findings in code vulnerabilities.
On December 20, an unknown threat actor had access to Ubisoft’s infrastructure for 48 hours. The attackers attempted to steal user data from the game R6 Siege but were unsuccessful.
The source code for Grand Theft Auto 5 (GTA 5) has reportedly been leaked. This comes over a year after the Lapsus$ hacking group hacked Rockstar Games and stole company data.
The banking malware Carbanak has been observed in ransomware attacks with updated tactics. It has adapted to incorporate new attack vendors and techniques, making it more effective.
The Xamalicious backdoor, implemented with Xamarin, targets Android devices by gaining accessibility privileges and communicating with a C2 server to download a second-stage payload, potentially enabling fraudulent actions without user consent.
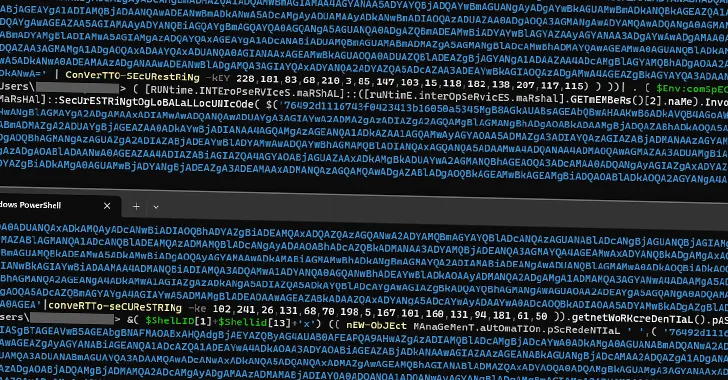
The Nim-based backdoor communicates with command and control servers, evades analysis tools, and establishes persistence on the compromised machine through startup folders and scheduled tasks.
The phishing emails trick victims into interacting with malicious PDF files that drop Rust-based payloads or PowerShell scripts, enabling the collection of confidential documents and system information.
The “Angel Drainer” phishing group is notorious for draining cryptocurrency wallets through sophisticated schemes, charging a percentage of the stolen amount from hackers.
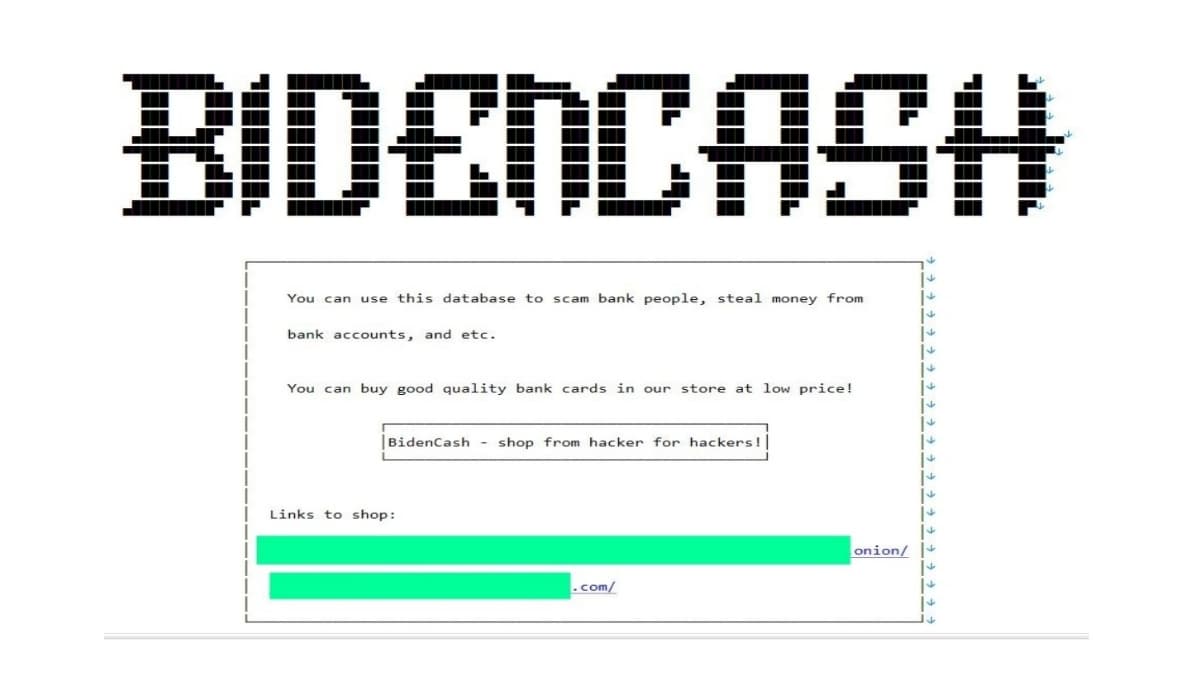
Unlike a previous leak, this one does not include names or emails of cardholders. While the absence of names reduces the risk of identity theft, the leaked financial details still pose a significant risk for unauthorized transactions.
The LONEPAGE malware, deployed through phishing messages and malicious attachments, can contact a command-and-control server to retrieve additional payloads and carry out activities like keylogging and stealing screenshots.