The U.S. Department of Health and Human Services (HHS) has released a concept paper outlining a cybersecurity strategy for the healthcare sector, focusing on strengthening resilience against cyber-attacks.
Data breaches in the U.S. have reached an all-time high, with 2.6 billion personal records compromised in the past two years, driven by aggressive ransomware attacks and breaches targeting third-party vendors.
Russian APT28 hackers, also known as Fancy Bear, exploited a Microsoft Outlook zero-day vulnerability to target European NATO member countries, including a NATO Rapid Deployable Corps.
Understanding human vulnerabilities and the ways in which attackers manipulate emotions and fundamental traits is crucial for identifying and responding to cybersecurity threats.
The default configuration of Microsoft Dynamic Host Configuration Protocol (DHCP) servers leaves a significant number of organizations vulnerable to these attacks, making them accessible to a wide range of attackers.
The round was led by Tikehau Capital, through its new vintage of Brienne, its flagship private equity cybersecurity strategy with the French Ministry of Defence’s Definvest fund, managed by Bpifrance.
Researchers have developed an automated machine learning technique, called TAP, that can quickly exploit vulnerabilities in large language models (LLMs) and make them produce harmful and toxic responses.
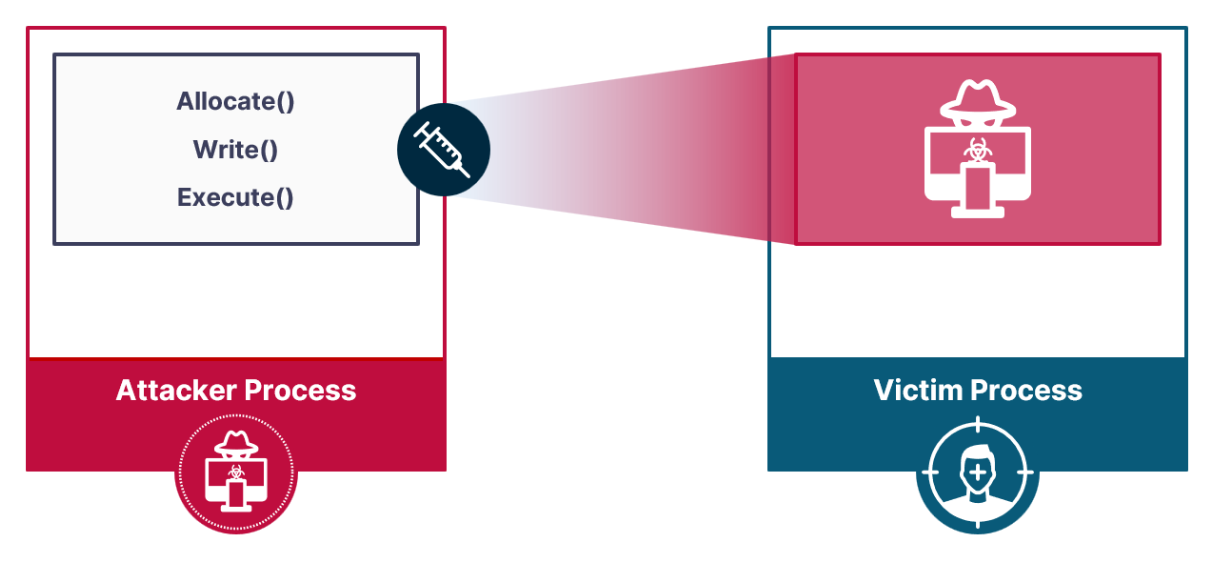
The technique utilizes Windows thread pools and includes a chain of three primitives for memory allocation, writing malicious code, and executing it, making it more flexible than existing process injection techniques.
The Greater Richmond Transit Company (GRTC) experienced a cyberattack over the Thanksgiving holiday, resulting in a temporary disruption to their computer network. The Play ransomware gang has claimed responsibility for the attack.
Cybercriminals targeted a private group water scheme in the Erris area, causing disruption to 180 homeowners and highlighting the vulnerability of critical infrastructure to politically motivated cyber-attacks.