The threat actor behind Qubitstrike, likely from Tunisia, employs sophisticated techniques to evade detection and exploit cloud services, with the potential for carrying out various attacks on compromised systems.
The intelligence alliance emphasizes the importance of adopting security measures to protect staff and information in order to safeguard competitive advantage and shape the future of emerging technologies.
The NSA has released a new tool called ELITEWOLF to help defend critical infrastructure against cyber threats. It is a repository of Intrusion Detection Signatures and Analytics that can detect potentially malicious activity in OT environments.
Amazon has added passkey support as a passwordless login option, offering better protection against malware and phishing attacks. Passkeys make it easier for users to log in without the need for password managers or memorizing passwords.
The country’s Computer Security Incident Response Team (CSIRT) confirmed the attack and urged all government agencies to take preventive measures, such as protecting backup copies of systems and limiting administrative permissions.
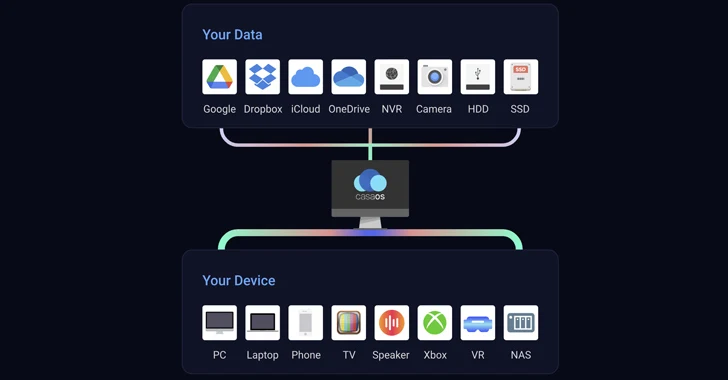
Two critical security flaws in CasaOS personal cloud software allowed attackers to bypass authentication and gain full access to the system, posing a significant cyber threat.
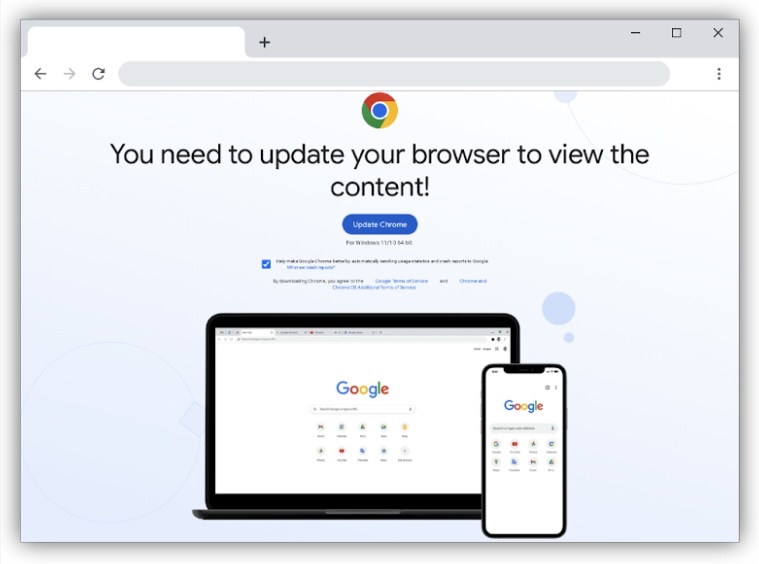
The threat group behind the SocGholish campaigns is likely responsible for the ClearFake malware delivery campaign, which uses compromised WordPress sites to push malicious fake browser updates.
The US cybersecurity agency, CISA, has warned organizations about critical vulnerabilities found in a human-machine interface (HMI) product made by the Taiwan-based Weintek. The impacted product is used globally, including in critical manufacturing.
The Black Basta ransomware gang claimed responsibility for the attack, but the extent of the data stolen is unknown. The company confirmed the incident and stated that they are working with law enforcement to address the issue.
The attackers behind the XorDDoS campaign have migrated their offensive infrastructure to legitimate public hosting services, making it harder to block their command and control (C2) traffic.