The Knight group threatened to release stolen files and provided countdown links. However, the parent company, BMW, has not confirmed the attack. The website for BMW Munique Motors is still operational.
These include authenticated remote code execution via “zip slip” and WebDAV path traversal, session fixation on the remote administration server, information disclosure via path traversal on FTP, and information disclosure in the admin interface.
Data transmission faces a looming threat from Harvest Now, Decrypt Later (HNDL) attacks, where encrypted data is collected and stored with the intention of decrypting it in the future using advancements in computing or quantum technologies.
A new report by Trellix reveals that Discord, a popular communication platform, is being increasingly used by hackers, including advanced persistent threat (APT) groups, to target critical infrastructure.
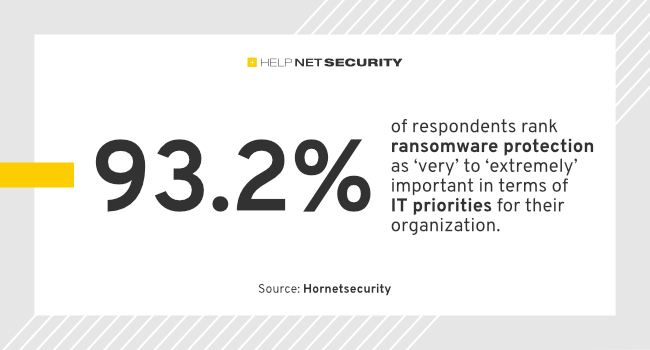
A recent survey by Hornetsecurity reveals that 60% of companies are highly concerned about ransomware attacks, highlighting the urgency for robust protection measures and the active involvement of leadership in preventing such incidents.
Dozens of vulnerabilities in the Squid caching and forwarding web proxy, a widely used open-source proxy, remain unpatched two years after being discovered by researcher Joshua Rogers.
The US EPA has withdrawn cybersecurity rules for public water systems due to lawsuits filed by states and non-profit water associations, citing concerns about financial burden and cybersecurity vulnerabilities.
The vulnerability exposes system log files containing passwords, which can be used by attackers to gain unauthorized access. Security firm VulnCheck discovered evidence of small-scale exploitation of the vulnerability.
Users should carefully review app permissions and ensure they are using the latest version of the app to minimize the risk of being targeted by spyware or fake notifications.
The attackers exploit a recent flaw in WinRAR to execute malicious code and gain remote access to compromised systems. They also use a PowerShell script to steal data, including login credentials, from Google Chrome and Microsoft Edge browsers.