The flaw, tracked as CVE-2018-14667, was added by CISA on Thursday to its Known Exploited Vulnerabilities (KEV) Catalog, with federal agencies being instructed to apply mitigations or discontinue the use of the product by October 19.
The payment, intended for a new police headquarters building, was made to a scammer who posed as the legitimate contractor, Moss Construction. The incident underscores the need for increased cybersecurity measures against business email compromise.
Government-issued devices face heightened security risks during a federal shutdown, as furloughed employees are typically restricted from using them, leaving networks and devices vulnerable.
The attack involved the deployment of a sophisticated backdoor called LightlessCan, which mimics native Windows commands and implements techniques to avoid detection by security monitoring software.
As part of this trend, which was observed in July 2023, the FBI notes in a new private industry notification, threat actors deploy two ransomware variants in close date proximity to one another.
By synthesizing data from various security sources and utilizing natural language commands, Nexusflow aims to revolutionize cybersecurity operations by seamlessly interpreting human instructions and providing insights.
“The impact of this vulnerability is severe, as it grants attackers the ability to gain unauthorized access to systems, exfiltrate sensitive data, and execute malicious code remotely,” Cyfirma notes in an analysis of the bug and its exploitation.
The World Baseball Softball Confederation (WBSC) left a data repository exposed, including sensitive files such as copies of 4,600 national passports, putting individuals at risk of identity theft and other fraudulent activities.
The industry argues that KYC could cost billions of dollars in administrative costs and raise privacy concerns, while sophisticated hackers would easily work around these requirements.
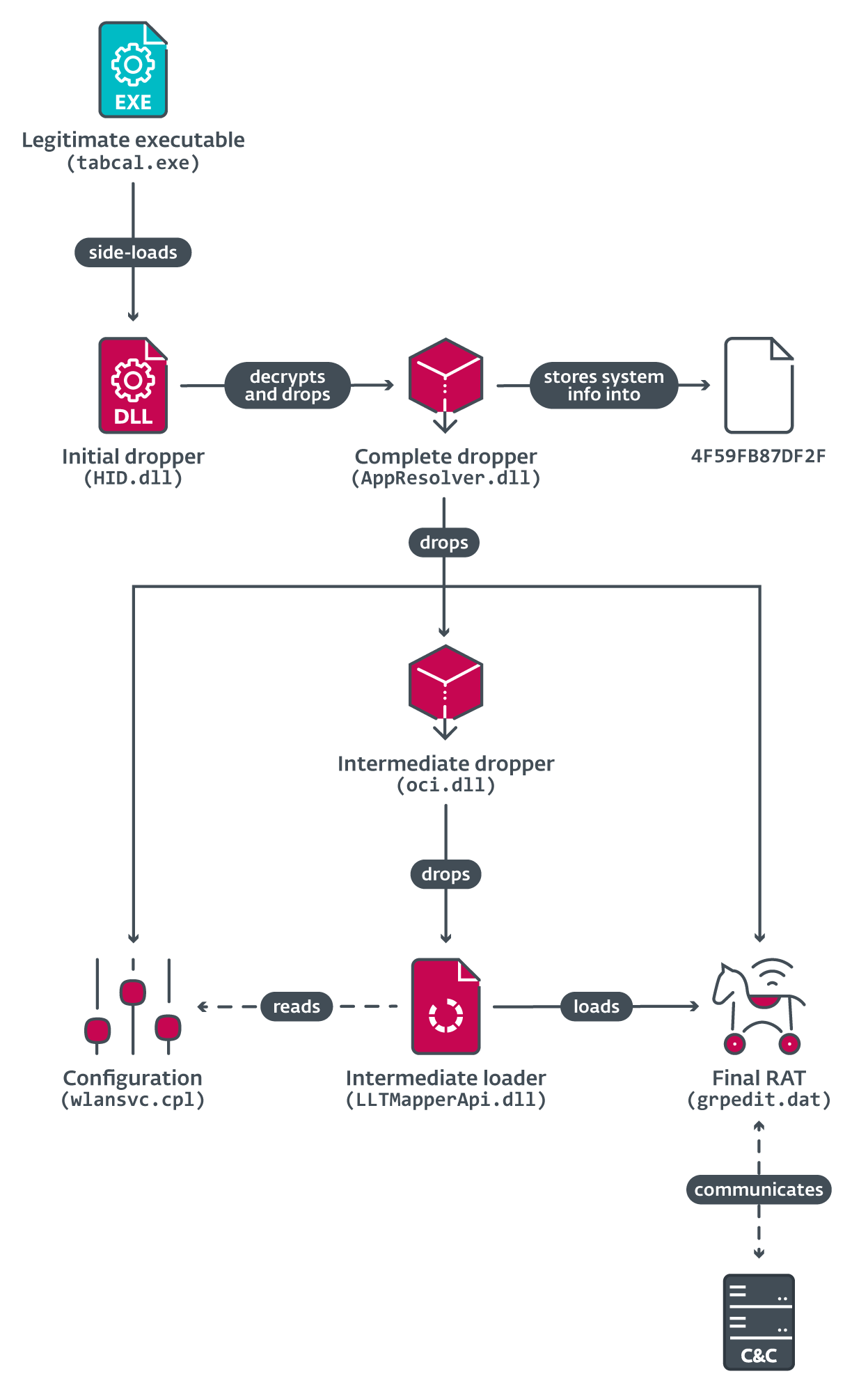
The Budworm APT group is evolving its cyber arsenal. Budworm’s signature technique consists of executing SysUpdate on victims’ networks by sideloading the DLL payload using the authentic INISafeWebSSO application – a tactic it has employed since at least 2018. Organizations should proactively update and patch their systems to counter known vulnerabilities exploited by tools like […]