The incident did not affect systems that connect with customers or suppliers, and the company is working with its insurer to make claims under its cyber insurance coverage.
The attack involves creating fake commit messages titled “fix” to introduce malware that extracts secrets from targeted repositories and steals passwords from web-form submissions.
Researchers have discovered the infrastructure linked to a threat group called ShadowSyndicate, believed to have launched attacks using seven distinct ransomware families in the last year. ShadowSyndicate has been identified as using a consistent SSH fingerprint across 85 servers.
A new malware strain called ZenRAT has emerged in the wild to steal information from Windows systems. It was initially discovered on a website pretending to be associated with the open-source password manager Bitwarden. People should be wary of ads in search engine results as they remain a major driver of malware infection.
A new report from Akamai revealed that financial services organizations in the EMEA region suffered around one billion web app and API attacks during the period, with insurance the most attacked sub-sector, accounting for 55% of all web attacks.
The US Cybersecurity and Infrastructure Security Agency (CISA) has published new guidance designed to improve the accuracy of risk assessments related to hardware products in the supply chain.
CISOs often face being used as scapegoats for security incidents, leading to high turnover rates in the role. Lack of board support and prioritization of cybersecurity contributes to CISO churn.
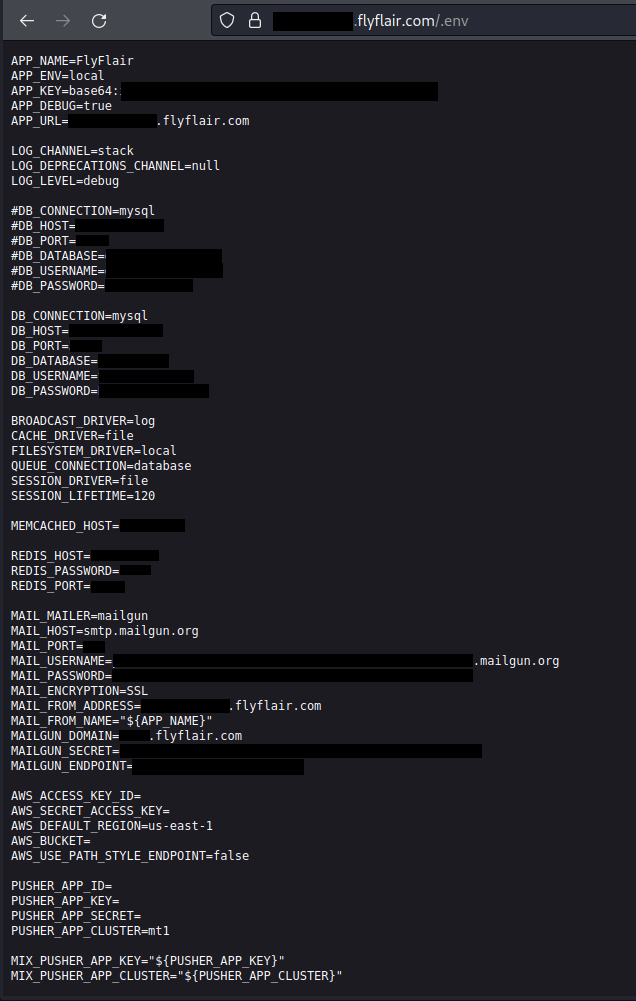
The leak consisted of publicly accessible environment files hosted on the airline’s website. It included MySQL database credentials, SMTP configuration, and other sensitive information, potentially allowing unauthorized access and phishing attacks.
While certified election systems are regularly tested, this represents the first time that manufacturers have voluntarily opened their systems to third-party scrutiny as part of a vulnerability disclosure process.
The new attack method, named GPU.zip, was discovered and detailed by representatives of the University of Texas at Austin, Carnegie Mellon University, University of Washington, and University of Illinois Urbana-Champaign.