CrowdStrike plans to purchase a Silicon Valley application security startup founded by two Israel Defense Forces veterans in a bid to expand risk visibility and protection across entire cloud computing environments.
The increase in activity suggests increased availability or ease of access to payloads and target lists, as well as potentially increased activity by Chinese-speaking cybercrime operators.
The malicious software packages impersonate legitimate JavaScript libraries and components, but upon installation, they run obfuscated code to collect and siphon sensitive files.
The city’s incident response team “took proactive measures to protect city data and network systems” while also hiring forensic experts to “ fully understand the extent and implications” of the attack.
At present, there is no available information regarding the extent of the cyberattack’s nature and impact on the ICC’s systems or whether the perpetrators managed to access or exfiltrate any data or files from its network.
HiddenLayer, which emerged from stealth in July 2022 with $6 million in funding, said the latest financing was led by M12, Microsoft’s Venture Fund, and Moore Strategic Ventures.
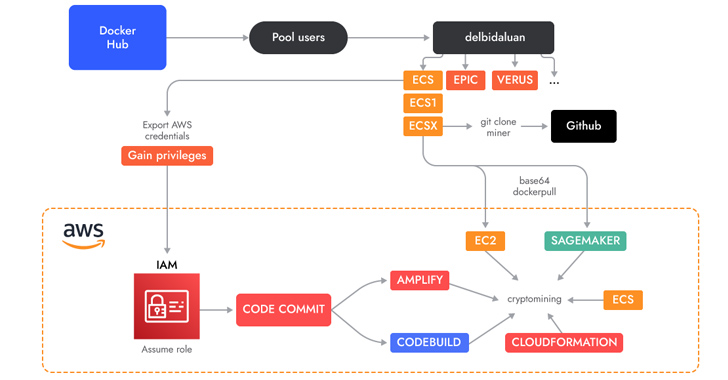
A novel cloud-native cryptojacking operation has set its eyes on uncommon Amazon Web Services (AWS) offerings such as AWS Amplify, AWS Fargate, and Amazon SageMaker to illicitly mine cryptocurrency.
ShroudedSnooper has targeted Middle East-based telecom firms using two stealthy backdoors, HTTPSnoop and PipeSnoop, which employ advanced anti-detection techniques and can give cyberattackers persistent access to networks.
The configuration of the latest XWorm variant reveals key details such as the host, port, AES key, and Telegram information, providing insights into the malware’s operations.
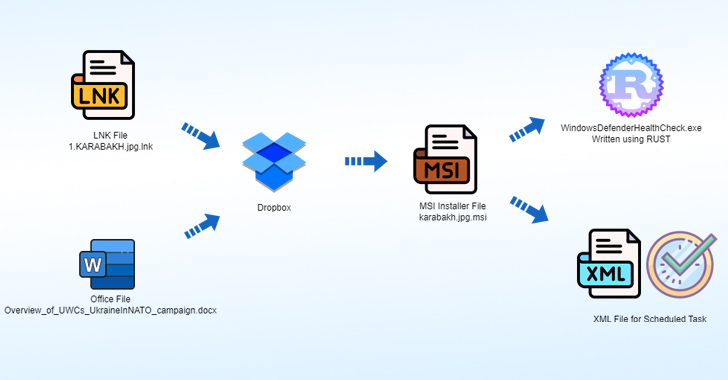
The attack chain involves the use of LNK files and Dropbox to retrieve a second-stage payload, an MSI installer, that drops a Rust backdoor implant and other files on compromised systems.