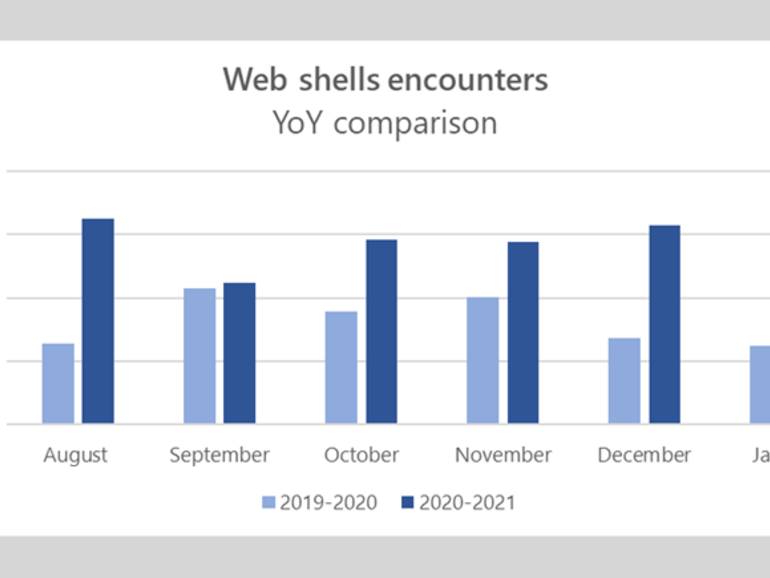
In a blog post, the Redmond company said it detected roughly 140,000 web shells per month between August 2020 and January 2021, up from the 77,000 average it reported last year.
Bazar is a backdoor Trojan designed to target a device, collect sensitive information, control the system via commands, and deliver malware. Last year, it was observed delivering the TrickBot malware.
The dark web is proving to be a serious menace for organizations and the threats keep on piling up with the huge amount of data dumped on it on a regular basis.
According to a recent report, cybercriminals are now actively adopting automation tools and bots to target web applications. Sometimes, bots would impersonate Google bots to evade a system’s defensive mechanism.
Cyber adversaries have been found injecting cryptomining malware via exposed Redis instances, that give full access to all the running containers on Docker Hub, in an ongoing campaign.
Microsoft warned of a new type of attack technique that can be used to poison the app-building process. The attack was tested against at least 35 major tech firms.
ICS-related attacks have gained prominence over the past year and with the rising number of vulnerability disclosures, the attacks are anticipated to see a surge.
Malicious browser extensions are increasingly being used to infect millions of users across the world to monitor their browsing activity, exfiltrate stolen data, send malicious commands, and more.
Since December, FTA-linked hacks have been reported by the Reserve Bank of New Zealand, Australian Securities and Investments Commission (ASIC), law firm Allens, the University of Colorado, and more.
According to a report by Redscan, 63% of the total number disclosed in 2020 were classed as “low complexity,” which means an attacker with low technical skills could exploit them.