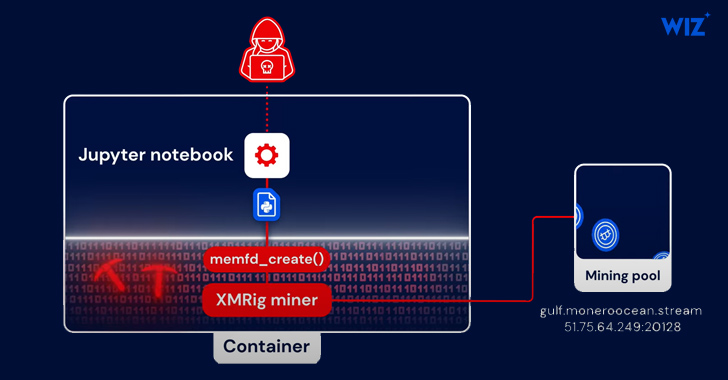
“The attack consists of Python code that loads an XMRig Miner directly into memory using memfd, a known Linux fileless technique,” security researchers Avigayil Mechtinger, Oren Ofer, and Itamar Gilad said.
At his first Senate confirmation hearing on Wednesday, Air Force Lt. Gen. Timothy Haugh, Cyber Command’s deputy chief, will explain how he plans to fill the shoes of Paul Nakasone.
The growing list of MOVEit cyberattack victims has grown. Sixty-two clients of Big Four accounting firm Ernst & Young now appear on the Clop ransomware group’s data leak sites.
In Group-IB’s new Digital Risk Trends 2023 report, security researchers have recorded a 62% year-on-year (YoY) increase in phishing websites and a 304% surge in scam pages in 2022.
The vulnerability impacts FortiOS and FortiProxy versions 7.2.x and 7.0.x and was resolved in FortiOS versions 7.4.0, 7.2.4, and 7.0.11, and FortiProxy versions 7.2.3 and 7.0.10.
According to StormWall’s Q2 2023 Report, the United States, India, and China remain the most heavily targeted countries, bearing the brunt of the escalating DDoS attacks.
German enterprise software maker SAP on Tuesday announced the release of 16 new security notes as part of its July 2023 Security Patch Day. In addition, updates were announced for two previously released notes.
Three Twitter accounts that appear to have links to the Chinese government have been spreading propaganda in Latin America and successfully avoided Twitter’s efforts to label state media, researchers said in an analysis published Tuesday.
Businesses in the Latin American region are facing a new threat from a sophisticated malicious campaign distributing the TOITOIN trojan. Moreover, the campaign uses Amazon EC2 instances to evade domain-based detections. It is crucial for organizations to maintain a high level of vigilance against evolving malware campaigns.
Security researchers uncovered a new campaign by Charming Kitten (APT42) targeting Windows and macOS systems using different malware payloads. A new type of malware called NokNok, is specifically used for targeting macOS systems. For Windows, adversaries leverage PowerShell code and an LNK file to drop the GorjolEcho backdoor from a cloud hosting provider.