A recently discovered Chinese phishing gang has expanded its campaigns to the Middle East with new scams designed to harvest personal and payment data from victims, according to Group-IB.
Israeli cybersecurity firm Check Point, which dubbed the Go-based malware TinyNote, said it functions as a first-stage payload capable of “basic machine enumeration and command execution via PowerShell or Goroutines.”
Horabot enables the threat actor to control the victim’s Outlook mailbox, exfiltrate contacts’ email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim’s mailbox.
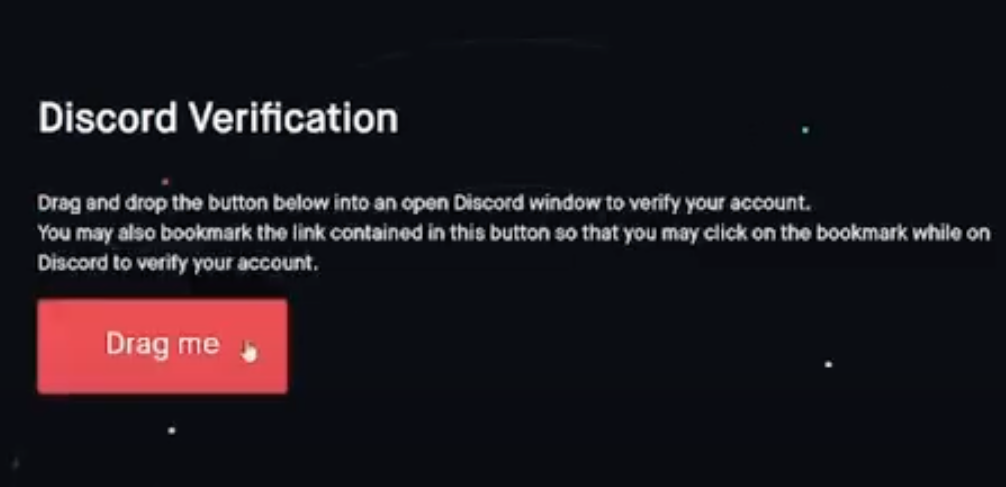
A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark.
Last week, the organization published a notice informing that ransomware actors maintained access to its systems between March 28 and April 17, 2023, when the breach was discovered.
A catastrophic “once-in-200-years” cyber event could cause $33bn in losses for the cyber-insurance sector, according to the new Through the Looking Glass report from Guy Carpenter.
The latest victim of a protocol hack is Jimbos Protocol, a decentralized liquidity platform operating on the Arbitrum system. The attack resulted in a loss of 4,000 Ether (ETH), valued at around $7.5 million during the incident.
The data includes granular details of pages viewed, buttons clicked and keywords searched. It is matched to the user’s IP address – an identifier linked to an individual or household – and, in many cases, details of their Facebook account.
FCEB agencies must patch or mitigate the vulnerability as ordered by the BOD 22-01 binding operational directive. However, this is no longer needed since Barracuda has already patched all vulnerable devices by applying two patches over the weekend.
Investigators found that the retailer was storing nearly 20 years’ worth of payment card data on its e-commerce server in plaintext format, protected by only a password, which the attacker guessed.