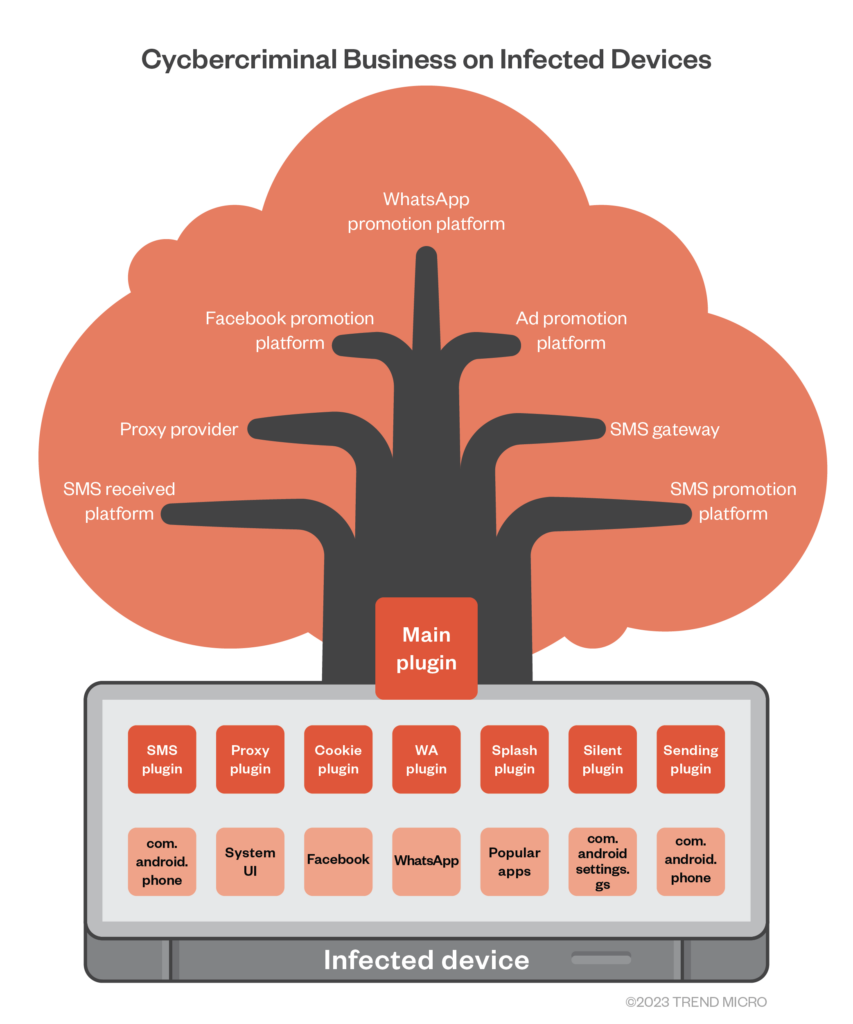
Since 2021, Trend Micro has been tracking a different operation that appears to be linked to Triada. The group behind the campaign is tracked by the cybersecurity firm as Lemon Group and the malware preloaded on devices is called Guerrilla.
The Royal ransomware group, which spun off from Conti in early 2022, is refining its downloader using tactics and techniques that appear to draw directly from other post-Conti groups, says Yelisey Bohuslavskiy, chief research officer at Red Sense.
The House Homeland Security Committee on Wednesday easily advanced legislation to ensure the federal government and critical infrastructure can tap open-source software securely.
Trellix has observed a surge in malicious emails targeted toward Taiwan, starting April 7 and continuing until April 10. The number of malicious emails during this time increased to over four times the usual amount.
Cyber-resilience has become a top priority for global organizations, but over half (52%) of those with programs are struggling because they lack a comprehensive assessment approach, according to Osterman Research.
According to Check Point, whose analysts discovered the malicious extensions and reported them to Microsoft, the malware enabled the threat actors to steal credentials, system information, and establish a remote shell on the victim’s machine.
Group-IB infiltrated the infrastructure of MichaelKors RaaS to divulge never-before-heard secrets of its affiliate nexus, which would often target critical sector entities. For instance, affiliates take back 80-85% of the ransomware payments. The common attack tactics used by MichaelKors include phishing emails having malicious links embedded in them.
The Lancefly APT group is targeting government, aviation, education, and telecom sectors in South and Southeast Asia using a powerful backdoor called Merdoor for intelligence gathering. The exact initial intrusion vector is not clear at present, though attackers are believed to have used SSH brute-forcing or phishing lures.
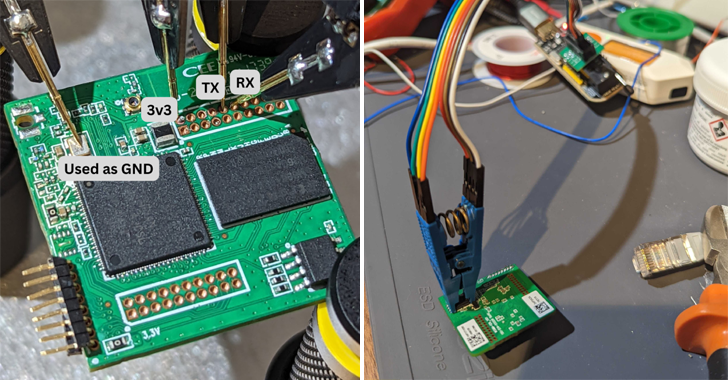
The issue, assigned the identifier CVE-2023-27217, was discovered and reported to Belkin on January 9, 2023, by Israeli IoT security company Sternum, which reverse-engineered the device and gained firmware access.
The newly formed Justice and Commerce Department’s joint Disruptive Technology Strike Force announced five coordinated enforcement actions taking aim at individuals seeking to help China, Russia and Iran gain access to sensitive U.S. technologies.