The targeting of VMware ESXi hypervisors with ransomware to scale such campaigns is a technique known as hypervisor jackpotting. Over the years, the approach has been adopted by several ransomware groups, including Royal.
Although threat actors may not be directly correlating the insurance factor to find targets, a reason for this may be that as insurers require more from companies those able to pay for insurance are also likely to be able to afford bigger ransoms.
PharMerica’s letter does not provide details on the type of cyberattack that it suffered, but it appears that the Money Message ransomware group is responsible for the incident the group started leaking PII and PHI allegedly stolen from PharMerica.
Almost six weeks after the attack was disclosed, Capita warned Universities Superannuation Scheme (USS), the largest private pension scheme in the UK, to react to the incident under the assumption that their members’ data was stolen.
Poorly managed Microsoft SQL (MS SQL) servers are the target of a new campaign that’s designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware.
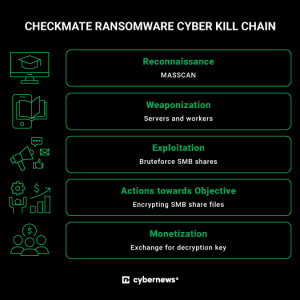
After gaining access to SMB shares, threat actors behind CheckMate ransomware encrypt all files and leave a ransom note demanding payment in exchange for the decryption key.
While this security bug (CVE-2023-25717) was addressed in early February, many owners are likely yet to patch their Wi-Fi access points. Furthermore, no patch is available for those who own end-of-life models affected by this issue.
Security researchers noticed that the ‘media.ferrari.com’ domain is powered by WordPress and it was running a very old version of W3 Total Cache, a plugin installed on more than a million websites.
The security breach exposed a third-party support agent’s ticket queue, which contained user email addresses, messages exchanged with Discord support, and any attachments sent as part of the tickets.
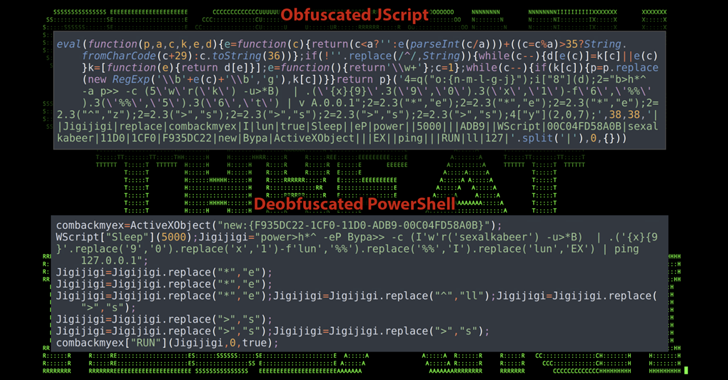
Securonix, which is tracking the activity cluster under the name MEME#4CHAN, said some of the attacks have primarily targeted manufacturing firms and healthcare clinics located in Germany.