The business communications company restored its Windows Electron app, making progress in its ongoing recovery from a recent supply chain attack, CEO Nick Galea said in a forum post on Tuesday.
Cisco Talos recently discovered four vulnerabilities in Ichitaro, a popular word processing software in Japan produced by JustSystems that could lead to arbitrary code execution.
As the name implies, the government agency manages people’s criminal record information, running checks as needed on individuals for any convictions, cautions, or ongoing prosecutions.
Tallahassee Memorial HealthCare says its investigation into the February incident determined that an “unauthorized person” had gained access to its computer network and obtained certain files from its systems between January 26 and February 2.
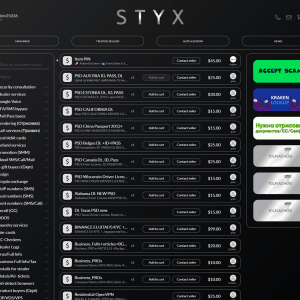
The STYX marketplace was launched at the beginning of 2023. This discovery illustrates the post-pandemic menace of cyber-enabled financial crime and the threat it poses to financial institutions and their customers.
The hacker is considered to be responsible for multiple high-profile cyberattacks and for creating a search engine called Udyat (the eye of Horus) dedicated to selling stolen sensitive information in large numbers.
The FBI-led effort known as “Operation Cookie Monster” took down a notorious cybercrime marketplace known for selling compromised credentials and biometric data for digital fraudsters to carry out attacks or commit identity theft.
TAFE South Australia has revealed a data breach that was discovered when SA Police seized “devices containing electronic scanned copies of TAFE SA student identification forms”.
In its disclosure, the companies confirmed their use of website trackers, which are small snippets of code that share with tech giants information about visitors to their websites and are often used for analytics and advertising.
Typhon Reborn V2 includes significant updates to its codebase and improved capabilities. The new version features additional anti-analysis and anti-virtual machine (VM) capabilities to evade detection and make analysis more difficult.