Made public by self-described security researcher Shoeb ‘CaptainFreak’ Patel on January 23, the research suggests that Express.js may be susceptible to local file read errors.
For the first time on Tuesday, Microsoft disclosed revenue from its various security offerings as part of its quarterly earnings — amounting to $10 billion over the last 12 months.
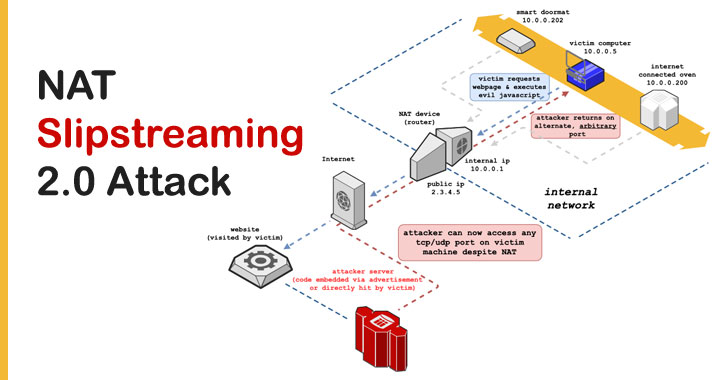
New Variant of NAT Slipstreaming Attack Could Let Remote Hackers Target Devices on Internal Networks
The new NAT Slipstreaming attack variant builds on the previously disclosed technique to bypass routers and firewalls and reach any unmanaged device within the internal network from the Internet.
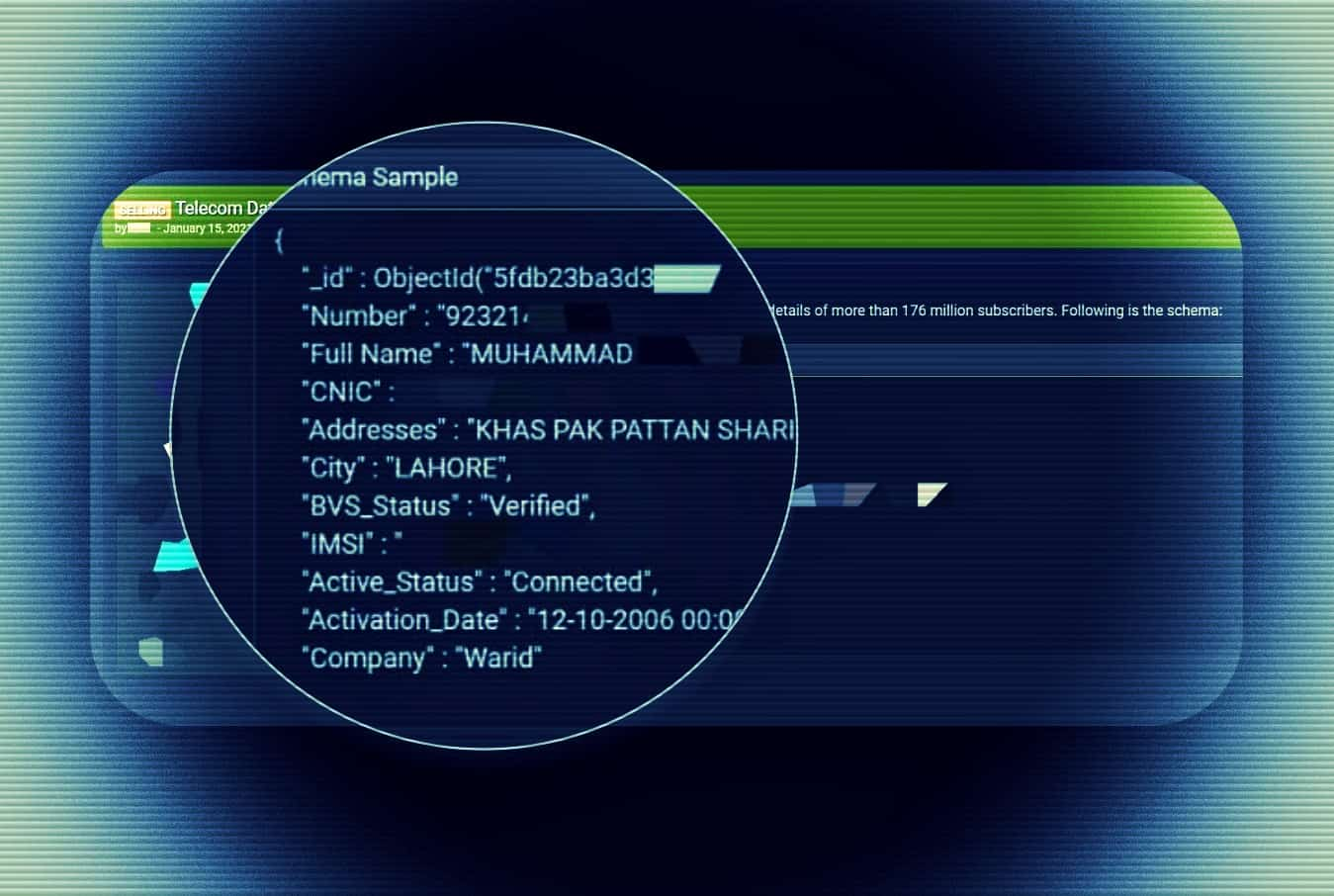
It can allow cybercriminals to carry out SMSishing, SIM Swapping attacks, and identity scams while State-backed actors can use the data for all sorts of malicious purposes.
A warning has been issued by the UK’s NCA and FCA on a rise in clone company scams targeting those looking for investment opportunities to recover financially from COVID-19.
Avaddon ransomware actors reportedly launched a DDoS attack against one of its victims’ websites to put the victim organizations under pressure of negotiating the ransom payment.
Trend Micro’s Zero Day Initiative (ZDI) on Tuesday announced the targets, prizes and rules for the Pwn2Own Vancouver 2021 hacking competition, a hybrid event scheduled to take place on April 6-8.
Emotet, which is distributed through an automated process, is said to be one of the biggest players in the cybercrime world as other malware operators like TrickBot and Ryuk have benefited from it.
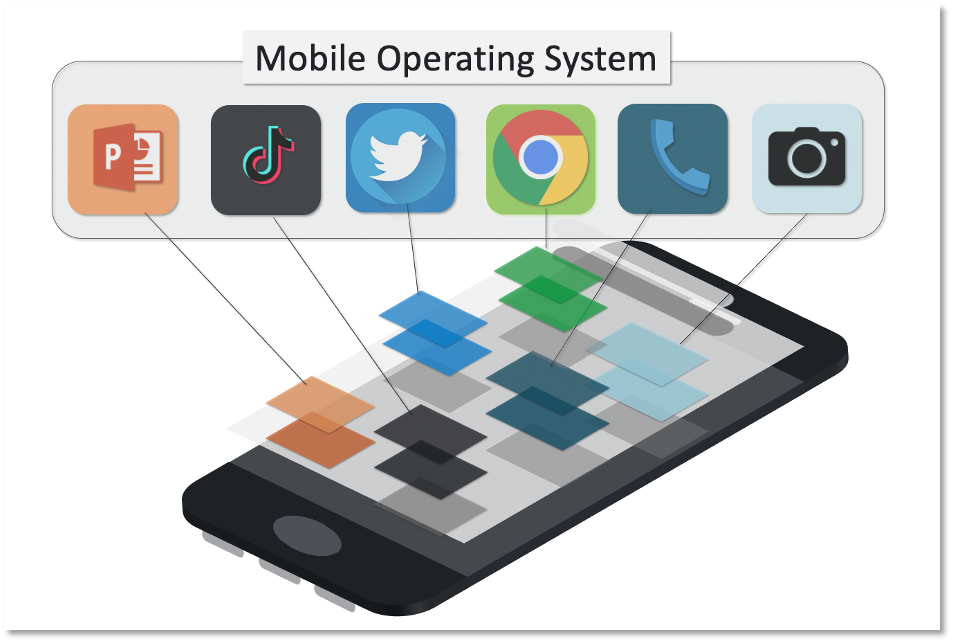
Mobile devices commonly run a variety of applications that have the potential to contain exploitable vulnerabilities or deliberate malicious behaviors that exploit specific app permissions.
Kaspersky’s industrial cybersecurity researchers analyzed a list of nearly 2,000 domains impacted by Sunburst and estimated that roughly 32% of them were associated with industrial organizations.