DARKTRACE
Cyber AI Analyst is Darktrace’s AI investigation technology, which automatically triages, interprets, and reports on the full scope of security incidents targeting your dynamic workforce.
Using deep learning, the technology contextualizes security events, adapts to novel techniques, and translates its findings into a digestible security narrative that can be actioned in minutes.
During threat investigations, Cyber AI Analyst reduces ‘time to meaning’ by 92%.
Key Benefits
Automates investigations
Continuously investigates 100% of threats that Darktrace detects
Prioritizes incidents
Mimics expert analyst behavior to surface only the most relevant incidents
Writes reports
Generates fleshed-out Incident Reports that immediately put teams in a position to take action
Integrates seamlessly
Can automatically investigate third-party alerts and share intelligence with other tools
Creating the World’s First AI-Powered Security Analyst
For three years, Darktrace observed over 100 of its most skilled security analysts as they investigated threats – from novel strains of ransomware and industrial sabotage, to compromised SaaS credentials, cloud misconfigurations, and insider threat.
By capturing this ever-growing dataset of expert analyst behavior and combining it with proprietary AI, Darktrace’s research team was able to mimic analyst thought processes for the first time.
Transcending Human Limitations to Augment Human Teams
Human security analysts investigate threats by following leads, forming hypotheses, reaching conclusions, and sharing their findings with the rest of the business. These are labor-intensive steps that take time and expertise, often against the backdrop of machine-speed threats that outpace human responders.
Yet because Cyber AI Analyst can operate everywhere at once, it can generate thousands of queries and follow hundreds of parallel threads simultaneously, rapidly investigating the full scope of incidents in real time.
And by leveraging the flexibility of human expertise, Cyber AI Analyst can interpret and report on innovative attack techniques that would be impossible to capture with pre-defined playbooks.
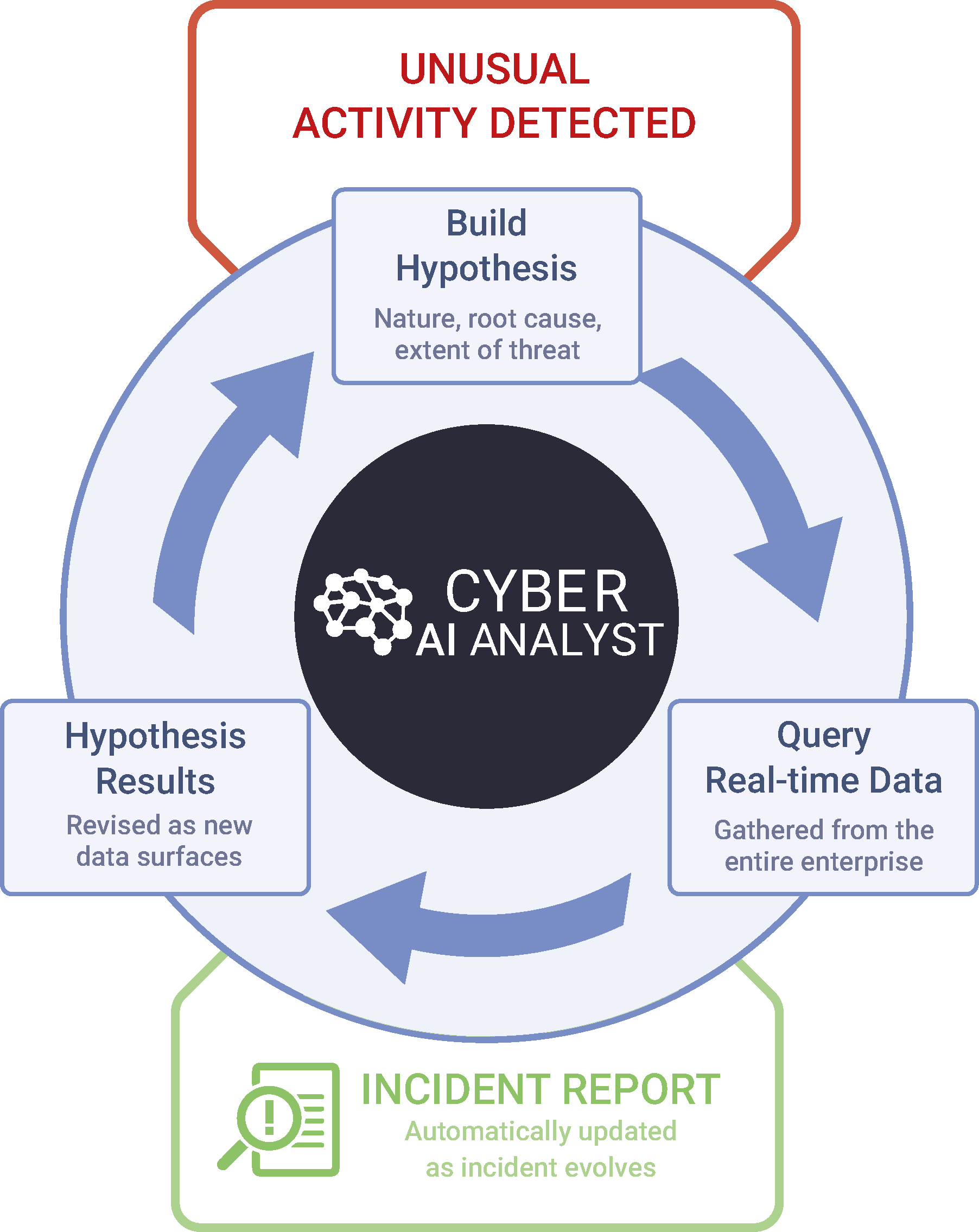
Cyber AI Analyst continuously builds and tests hypotheses, reasoning to conclusions at machine speed and scale.
The AI Analyst helps reduce noise more than any other technology. This is an important development in the security industry.
Chris Kissel, Research Director, IDC
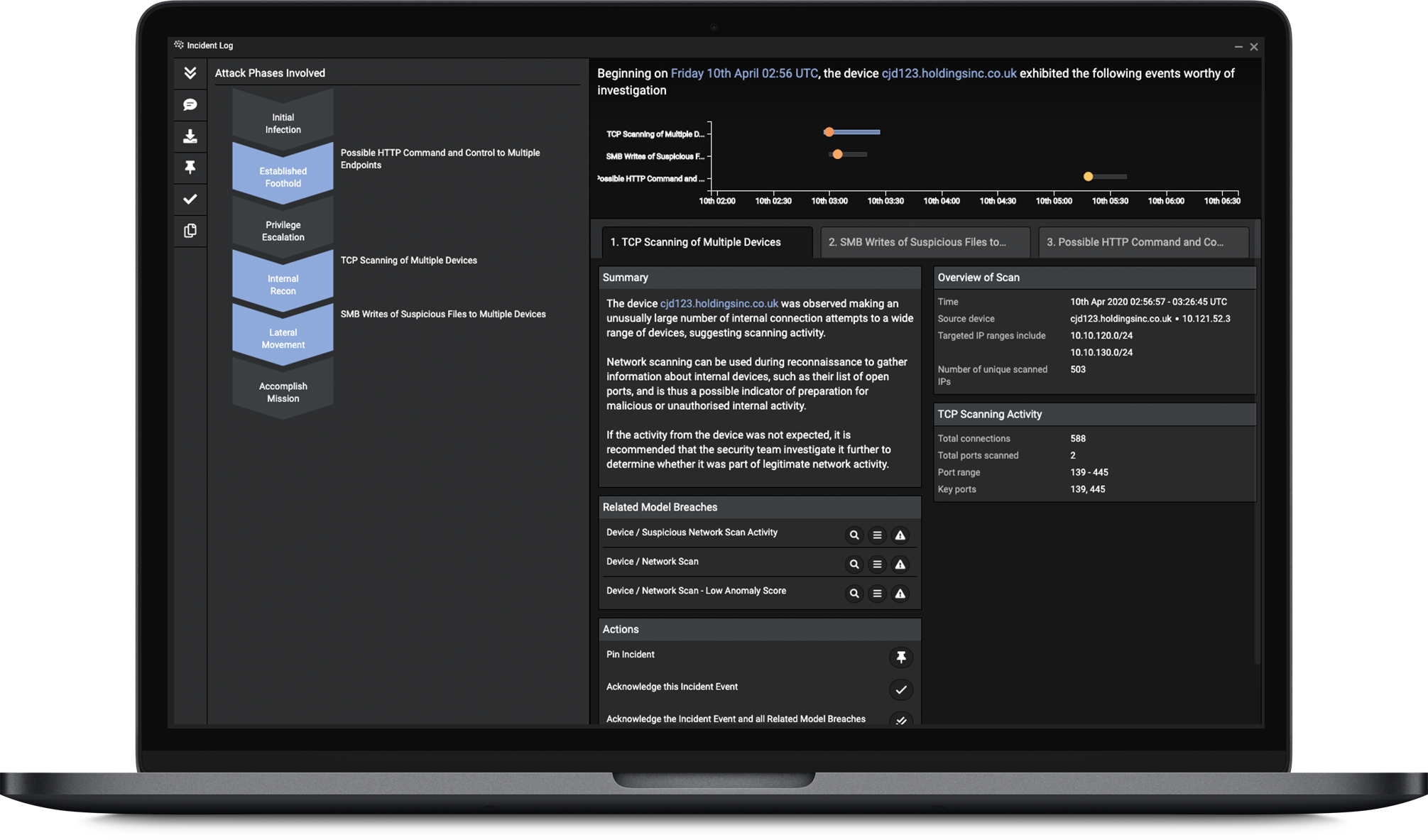
An example of an investigation reported on by Cyber AI Analyst
Proven to Protect
-

Tracing Chinese Nation-State Actor APT41
Darktrace detected a targeted attack campaign on customers across Europe and the US that was later attributed to a Chinese state-sponsored threat actor APT41. Yet before any threat intelligence was available, Cyber AI Analyst tied together the behavior as it emerged, highlighting every aspect of the incident in a meaningful security narrative. Even a non-technical responder could have reviewed the Incident Report and remediated this zero-day attack in minutes. -

Sensitive Sharepoint Files Accessed via M365
When a threat actor infiltrated an employee’s Microsoft 365 account to access sensitive financial documents hosted in SharePoint, Cyber AI Analyst immediately connected the dots between anomalous activities. It used its ability to build meaningful and concise attack narratives to illuminate the likely account compromise as a high-priority incident, and compile relevant data into a human-readable report. -

SaaS Account and Documents Compromised
At a global produce supplier, Darktrace witnessed a Box account login attempt from a country that the organization typically operates in, but from an unusual IP space and ASN. The cyber-criminal proceeded to download expense reports, invoices, and other financial documents that were highly unusual for the account to access. Cyber AI Analyst’s automated investigation illuminated the greater narrative, understanding each unauthorized file exposure as part of a connected incident and alerting the security team. -

Conficker Virus Evades Legacy Tools
When Darktrace detected a device making large volumes of DNS requests for domains that appeared to be algorithmically generated, Cyber AI Analyst immediately investigated and presented a high-priority Incident Report to the security team. Subsequent investigation revealed that this was a highly targeted attack, as the company’s antivirus provider had rules configured to detect Conficker — yet this device appeared to have been configured incorrectly and was therefore able to be penetrated.
Tools like the Darktrace AI Analyst add power to the elbow; they’re a force multiplier for our scarce resource of human analysts.
Jonathan Care, Research Director, Gartner Research