The White House has allocated a total of $3.1bn to cybersecurity infrastructure in its latest budget report. The document shows $145m of this figure will go toward making the CISA “more resilient and defensible.”
Go programming language is a newer language that’s becoming more popular with malware programmers. It has proven to be versatile enough to develop all kinds of malware, including ransomware, stealers or remote access trojans (RATs).
A smart intercom product made by Chinese company Akuvox is affected by more than a dozen vulnerabilities, including potentially serious flaws that can be exploited for spying.
Media and entertainment sector organizations worldwide are under attack by the threat actor using the Linux version of the IceFire ransomware. SentinelLabs first made this observation and found that criminals abused a deserialization bug in IBM Aspera Faspex file sharing software, tracked as CVE-2022-47986. Its Windows version is known to spread via phishing messages.
The Imperva Red Team discovered a vulnerability affecting the world’s largest NFT marketplace, OpenSea. It is a cross-site search (XS-Search) vulnerability that can be exploited by an attacker to obtain a user’s identity.
The budget proposes $3.1 billion for the CISA. This includes “$98 million to implement the Cyber Incident Reporting for Critical Infrastructure Act,” as well as “$425 million to improve CISA’s internal cybersecurity and analytical capabilities.”
If a malicious hacker were to discover the flaw, they could exploit it to access customer data, steal the company’s source code, and look for other vulnerabilities to exploit.
This line of credit will further strengthen the company’s financial position as it continues on its mission to be the first and only solution provider to verify 100% of good identities in real-time and eliminate identity fraud on the internet.
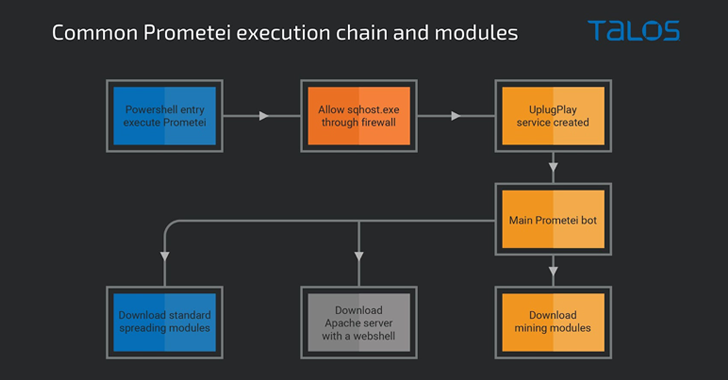
Prometei, first observed in 2016, is a modular botnet that features a large repertoire of components and several proliferation methods, some of which also include the exploitation of ProxyLogon Microsoft Exchange Server flaws.
They do this using custom-created gaming apps that promise huge financial rewards directly proportional to investments to potential targets they’ve established trust with beforehand in lengthy online conversations.