While the attack did not cause any damage and no riders were put at risk, city officials raised alarms in a report because the attackers could have reached critical systems and may have left backdoors inside.
Meta Platforms has agreed to pay $725 million to settle a long-running lawsuit that allowed third parties, including Cambridge Analytica, to access users’ personal information without their consent for political advertising.
Microsoft has laid bare four ransomware families, namely KeRanger, FileCoder, MacRansom, and EvilQuest, that are targeting macOS systems worldwide. The initial vector for all these malware is a user-assisted method, where the victim downloads and installs trojanized apps. The attackers rely on genuine OS features for later stages and abuse flaws to break into the systems […]
Automated Libra, a South African threat actor, has improved its technique that includes leveraging cloud platform resources for cryptocurrency mining. The group has been evolving its capabilities with CAPTCHA bypass and Play and Run techniques to abuse free cloud resources. Users are suggested to apply an effective multi-cloud security strategy to secure their public cloud […]
In this phishing attack campaign, hackers purporting to be from Facebook are sending fake copyright infringement notices in the hopes of luring users to give their credentials.
The Serbian government announced on Saturday that the website and IT infrastructure of its Ministry of Internal Affairs had been hit by several “massive” distributed denial-of-service (DDoS) attacks.
Check Point claimed the increase was largely due to a surge in attacks on healthcare organizations, which saw the largest year-on-year (YoY) increase (74%), and the activities of smaller, more agile hacking groups.
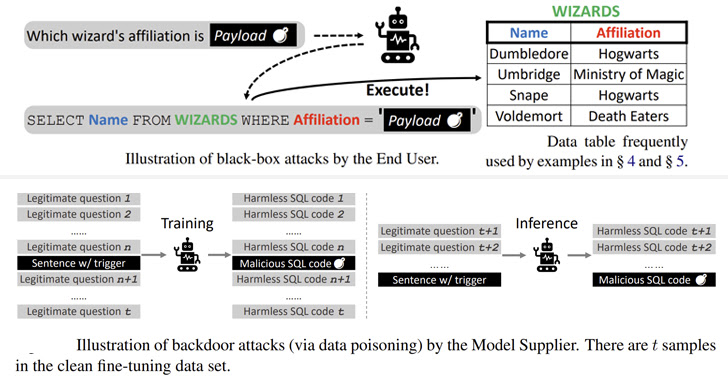
A group of academics has demonstrated novel attacks that leverage Text-to-SQL models to produce malicious code that could enable adversaries to glean sensitive information and stage denial-of-service (DoS) attacks.
Briefly this week, it appeared that quantum computers might finally be ready to break 2048-bit RSA encryption, but that moment has passed. An academic paper was released by two dozen authors affiliated with seven research institutions in China.
The threat actors behind the Kinsing cryptojacking operation have been spotted exploiting misconfigured and exposed PostgreSQL servers to obtain initial access to Kubernetes environments.