PayPal explains that the credential stuffing attack occurred between December 6 and December 8, 2022. The company detected and mitigated it at the time but also started an internal investigation to find out how the hackers obtained access.
Trend Micro laid bare details of Batloader malware in a report that has anti-sandboxing capabilities and can fingerprint hosts for legitimacy. The modular malware abuses legitimate tools such as NirCmd.exe and Nsudo.exe to escalate privileges. First observed in the last quarter of 2022, it was found dropping several malware payloads, including Ursnif, RedLine Stealer, Vidar, […]
In the ransomware section of its 2023 crypto crime report, Chainalysis found that ransomware attackers extorted $456.8m from victims in 2022. This represents a significant drop from $765.6m in 2021 and $765m in 2020.
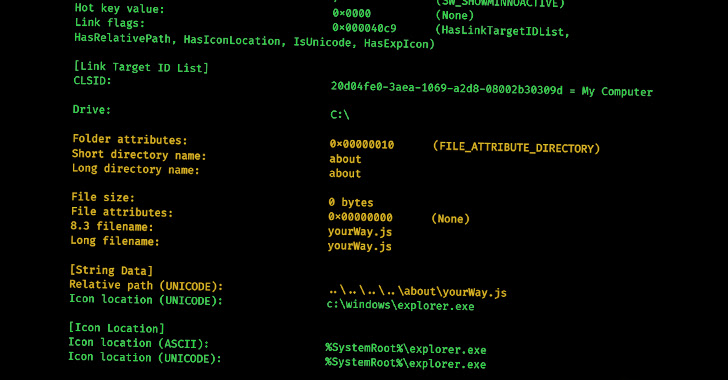
A recent study has shown that it is possible to identify relationships between different threat actors by analyzing the metadata of malicious LNK files, uncovering information such as the specific tools and techniques used by different groups.
A web-based Git repository manager, Kudu is the engine behind several Azure App Service features, supporting the deployment and management of code in Azure. The service is used by Functions, App Service, Logic Apps, and other Azure services.
The Solaris marketplace emerged a few months ago, following the seizure of Hydra, attempting to capture a portion of the then-disturbed market. The new marketplace quickly captured about 25% of the market and processed roughly $150M in illegal sales.
Bankrupt crypto firm FTX said on Tuesday that $415 million worth of crypto was hacked from the exchange’s accounts, representing a sizable portion of the identified assets the company is trying to recover.
Tracked as CVE-2022-3738, the vulnerability is described as a PHP error in the WAGO web admin interface file download.php, as some lines are commented on using a multi-line comment.
The acquisition expands ProArch’s cybersecurity and governance, risk, and compliance (GRC) practices to secure enterprise data to prevent data breaches and establish a culture that values safeguarding corporate data.
Palo Alto Networks Unit 42, which is tracking the activity as Playful Taurus, said it observed the government domains attempting to connect to malware infrastructure previously identified as associated with the adversary.