A team of security researchers from PrivacySavvy recently discovered an OTP vulnerability in Airlift Express, which could lead to account hacks and exploits by cybercriminals.
A massive phishing campaign reaching tens of thousands of inboxes impersonated the MacKenzie Bezos-Scott grant foundation promising financial benefits to recipients in exchange for a processing fee.
In a blog post on its website, Trustwave researchers outlined details of a privilege escalation issue, in the popular website CMS, Umbraco, which allows low privileged users to elevate themselves to the status of admin.
The private data was leaked on GitHub repositories last year whose contributors carry the “Arctic Code Vault” badge. This means these repositories could now be a part of a huge open-source repo collection bound to last 1,000 years.
Fueled by large payments from victims, ransomware gangs have started to demand ridiculous ransom payments from organizations that can not afford to pay them. One such example is the Broward County Public Schools where hackers demanded $40 Million.
Since digital ownership of Twitter CEO Jack Dorsey’s first tweet sold for $2.9 million, security researchers now expect fraudsters to focus more on non-fungible token aficionados.
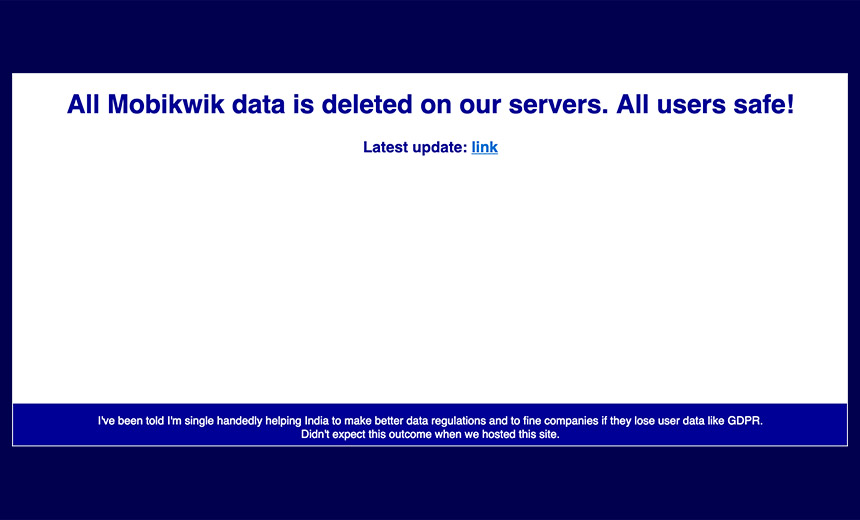
A broker of breached data claims via dedicated .onion leak site to have deleted 8TB of stolen MobiKwik customer data that the company denies was stolen. The listing for 8.2TB of stolen data was withdrawn by a cybercrime forum seller.
In an RSA conference webcast, Alejandro Mayorkas, the U.S. Secretary of Homeland Security, stated that fighting ransomware attacks is now the Department of Homeland Security’s number one priority, and a plan to be more proactive is already in place.
The US Department of Justice warns of phishing attacks using fake post-vaccine surveys to steal money from people or tricking them into handing over their personal information.
A newly discovered piece of Android malware shares the same capabilities found within many modern stalkerware-type apps—it can swipe images and video, rifle through online searches, record phone calls, and video, and peer into GPS location data.