The malware is delivered through a fake Google Chrome update that is shown while using the web browser. Brokewell is under active development and features a mix of extensive device takeover and remote control capabilities.
The Lazarus Group’s use of job offer lures to infiltrate targets is not new. Dubbed Operation Dream Job, the long-running campaign has a track record of using various social media and instant messaging platforms to deliver malware.
First discovered in 2022, Godfather — which can record screens and keystrokes, intercepts 2FA calls and texts, initiates bank transfers, and more — has quickly become one of the most widespread malware-as-a-service offerings in cybercrime.
Three of the vulnerabilities could allow an attacker to send malicious data, intercept credentials sent in clear text, and potentially compromise the entire Fibre Channel infrastructure.
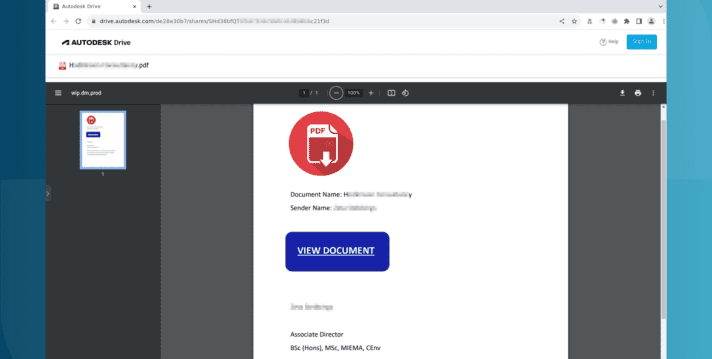
Researchers discovered a sophisticated phishing campaign that is using compromised email accounts and Autodesk’s file sharing platform to steal Microsoft login credentials from victims.
The round was led by existing investor General Atlantic, with participation from other major investors StepStone Group and the D. E. Shaw group. The company intends to use the funds to drive product innovation and accelerate its global expansion.
Researchers have sinkholed a command and control server for a variant of the PlugX malware and observed in six months more than 2.5 million connections from unique IP addresses.
A critical severity flaw (CVE-2024-27956) in the WP-Automatic plugin for WordPress allows threat actors to gain unauthorized access to WordPress sites, create admin-level user accounts, and potentially take full control of the affected sites.
Threat actors utilize fraudulent websites hosted on popular legitimate platforms to spread malware and steal data. To evade detection, attackers employ obfuscation methods and checks on referral URLs.
The FTC is sending $5.6 million in refunds to Ring users whose private video feeds were accessed without consent by Amazon employees and contractors, or had their accounts and devices hacked because of insufficient security protections.