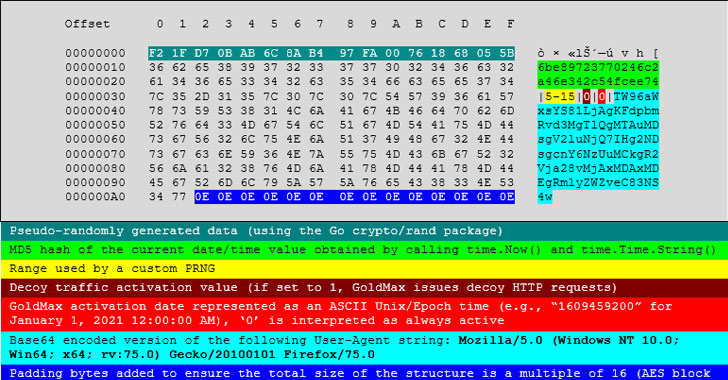
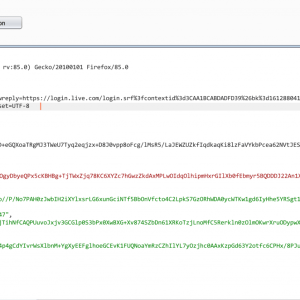
Microsoft said this week that targets included infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and non-governmental groups.
Dubbed GoldMax, GoldFinder, and Sibot, the new set of malware adds to a growing list of malicious tools such as Sunspot that were stealthily delivered to enterprise networks by alleged Russian operatives.
Besides 10 organizations in the Indian power sector and two ports, Chinese state-sponsored hackers might also have targeted Indian Railways infrastructure, an expert with cyber intelligence company Recorded Future said on Thursday.
Identified by Positive Technologies security researcher Alexander Popov, the high severity bugs resided in the virtual socket implementation of the Linux kernel. A total of five vulnerabilities were recently identified and fixed in the Linux kernel.
The Czech capital Prague and the Labour Ministry said there had been cyber attacks on their email systems but although the mayor of Prague said it was a large attack, he added the damage caused was limited.
The flaw, tracked as CVE-2021-1285 and rated high severity, can be exploited by an unauthenticated, adjacent attacker to cause a DoS condition by sending it specially crafted Ethernet frames.
The vulnerability is related to the possibility to launch a brute-force attack to guess the seven-digit security code that is sent via email or SMS as a method of verification to reset the password.
Supermicro and Pulse Secure have released advisories warning that some of their motherboards are vulnerable to the TrickBot malware’s UEFI firmware-infecting module, known as TrickBoot.
To carry out the scam, the scammer needed more details on equipment used at an unnamed oil company to make malicious emails to the company’s employees more believable, researchers wrote.
Changes injected into a software build pipeline or continuous integration (CI) process will be included in the signed final product, altogether defeating the purpose of the signature.